Navigating PCI DSS v4.0 with Comprehensive Threat Risk Assessments
The healthcare landscape is rapidly evolving, with mobile technology at the forefront of this transformation. The adoption of Mobile Electronic Health Records (Mobile EHR) systems holds significant promise. For example, it offers enhanced patient care, improved clinician efficiency, and greater operational flexibility. However, this shift also introduces significant cybersecurity challenges, particularly when sensitive patient data, including payment information, is involved. Ensuring Secure Mobile EHR is paramount, and for organizations handling cardholder data, compliance with the Payment Card Industry Data Security Standard version 4.0 (PCI DSS v4.0) becomes a critical consideration. A robust approach, underpinned by thorough Threat Risk Assessments (TRAs), is essential to navigate this complex environment.
Indeed, accessing patient records on tablets and smartphones offers undeniable convenience, empowering healthcare professionals to deliver timely care. However, it also expands the attack surface. Lost or stolen devices, insecure Wi-Fi connections, and vulnerable mobile applications can expose sensitive data. This exposure can lead to severe penalties, financial loss, and breached patient trust.Therefore, a proactive and comprehensive security strategy is a necessity, not a luxury, for any healthcare organization embracing mobile EHR. This article will explore methods for fortifying your Secure Mobile EHR practices, specifically examining alignment with PCI DSS v4.0 and the effective leveraging of detailed Threat Risk Assessments.
Understanding the Interplay: Mobile EHR, PCI DSS v4.0, and TRAs
Before diving into solutions, it’s crucial to understand the components at play and their intricate relationships. Mobile EHR refers to the use of mobile devices like smartphones and tablets to access, manage, and input electronic health records. The benefits include enhanced data accessibility for clinicians, improved workflow efficiency through real-time data entry, and potentially better patient engagement. However, these benefits come with inherent risks. Device loss or theft is a primary concern, as portable devices are more susceptible to being misplaced or stolen, potentially exposing electronic Protected Health Information (ePHI). Statistics from a 2023 healthcare breach report indicated that 15% of breaches involved lost or stolen devices.
Connecting to public or unsecured Wi-Fi networks can expose data in transit, and poorly secured mobile EHR applications or other vulnerable third-party apps on the device can create backdoors for attackers. Mobile devices are also increasingly targeted by malware and sophisticated phishing attacks. Achieving a truly Secure Mobile EHR environment requires addressing these risks head-on. While HIPAA governs the privacy and security of PHI, PCI DSS v4.0 specifically addresses the security of cardholder data. Healthcare organizations that accept credit or debit card payments fall under its purview. Even if the mobile EHR device itself doesn’t directly process payments, its presence within a network that handles cardholder data, or its integration with patient portals that have payment functionalities, can bring parts of the mobile environment into PCI DSS scope.
The Critical Role of Threat Risk Assessments (TRAs)
A Threat Risk Assessment (TRA) is a foundational cybersecurity activity involving the systematic identification of assets, threats to those assets, vulnerabilities that could be exploited by those threats, and the potential impact of such exploits. The goal of a TRA is to understand the organization’s risk posture and prioritize remediation efforts. In the context of Secure Mobile EHR and PCI DSS v4.0, TRAs are indispensable.
TRAs help organizations:
Identify specific threats to mobile EHR data and devices.
Uncover vulnerabilities in mobile infrastructure, applications, and processes.
Evaluate the likelihood and impact of potential security incidents.
Inform the selection and implementation of appropriate security controls to meet both general security needs and PCI DSS v4.0 requirements.
Support the “customized approach” allowed under PCI DSS v4.0 by providing the necessary risk-based justification for alternative controls.
A well-executed TRA provides the roadmap for a resilient and compliant Secure Mobile EHR strategy.
Navigating PCI DSS v4.0 Requirements for Secure Mobile EHR through TRAs
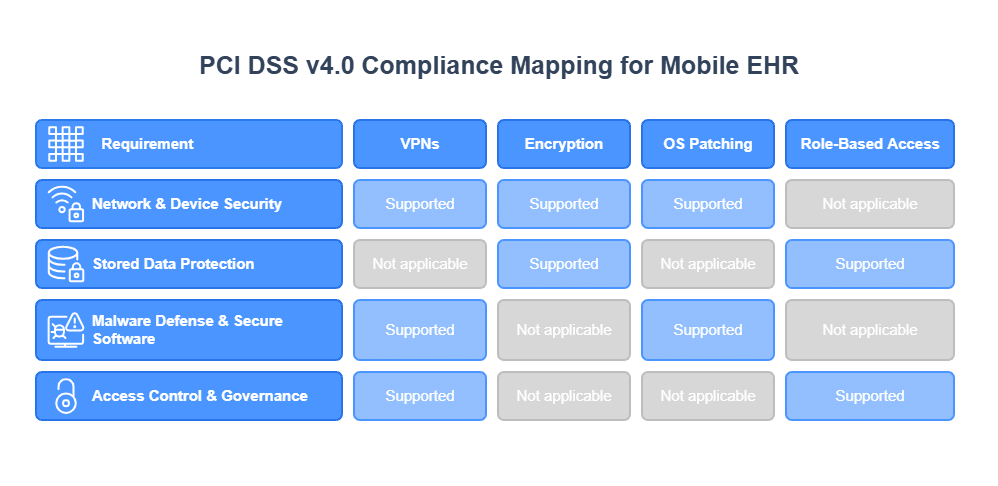
PCI DSS v4.0 comprises 12 core requirements. Several are highly relevant when mobile EHR devices operate within or connect to an environment handling cardholder data. TRAs are instrumental in determining applicability and compliance methods in these cases. For instance, Requirement 1 (Install and Maintain Network Security Controls) and Requirement 2 (Apply Secure Configurations) necessitate secure Wi-Fi configurations, VPNs for remote access, device firewalls, and secure configuration baselines for mobile devices. TRAs identify network vulnerabilities and misconfigurations on mobile devices, informing necessary controls like network segmentation.
Requirement 3 (Protect Stored Account Data) is critical. If any cardholder data is inadvertently stored or transmitted via the mobile EHR ecosystem, it must be protected via encryption, truncation, or tokenization. TRAs help identify where cardholder data might be present and assess risks, guiding data minimization. Requirements 5 (Protect All Systems and Networks from Malicious Software) and 6 (Develop and Maintain Secure Systems and Software) call for anti-malware solutions for mobile devices, secure app development for mobile EHR applications, and regular patching. TRAs identify vulnerabilities exploitable by malware and assess software risks, guiding patch management and application security decisions. Effective Posture and Vulnerability Management is key here.
Access Management and Organizational Security Framework
Requirement 8 of PCI DSS v4.0 (Identify Users and Authenticate Access to System Components) has key mandates. For instance, it requires strong, unique passwords for mobile EHR access. Additionally, it also mandates MFA for clinicians. Furthermore, it necessitates role-based access controls (RBAC) to limit access to ePHI and any associated cardholder data. TRAs evaluate the strength of current authentication mechanisms and identify risks from weak credentials, informing the implementation of robust Identity Management and Access Control.
Requirement 12 (Support Information Security with Organizational Policies and Programs) necessitates comprehensive security policies for mobile device usage (including BYOD if permitted), Incident Response plans for mobile-related breaches, and regular security awareness training. PCI DSS v4.0 specifically requires roles and responsibilities for each requirement to be assigned, documented, and understood. TRAs identify gaps in policies and training, helping refine incident response for mobile scenarios and allowing organizations to tailor their Audit and Compliance Management efforts effectively.
Conducting Effective TRAs for Secure Mobile EHR
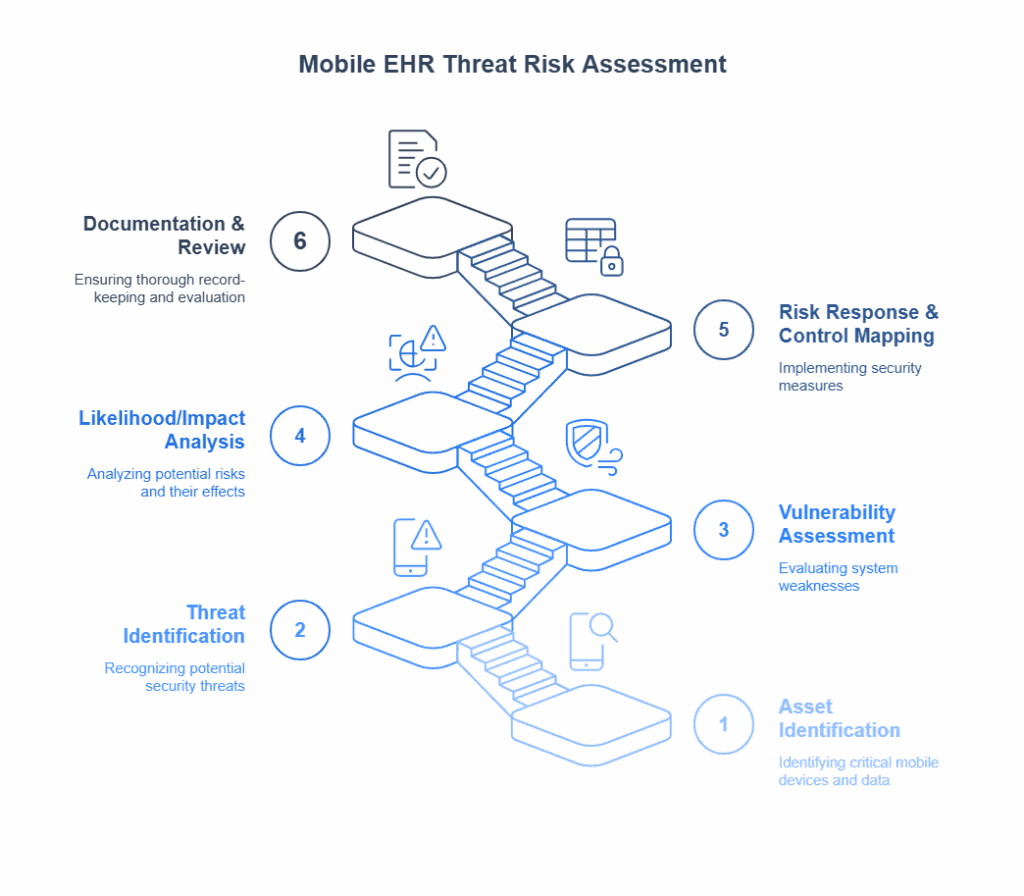
A TRA is a continuous process, not a one-time event, and for mobile EHR, it should be particularly dynamic. The TRA process involves several key stages:
Asset Identification: Catalog all mobile devices, applications, data, and network components involved in the mobile EHR ecosystem. Ensure a robust Asset Inventory and Management process is in place.
Threat Identification: Brainstorm potential threats specific to mobile environments (e.g., device theft, malware, insecure app stores, Wi-Fi sniffing, social engineering targeting mobile users). The Verizon Data Breach Investigations Report (DBIR) consistently shows that human error and social engineering are significant factors.
Vulnerability Assessment: Identify weaknesses in mobile devices, operating systems, applications, network configurations, and user practices. This includes reviewing device settings, app permissions, and encryption standards.
Likelihood and Impact Analysis: Determine the probability of each threat exploiting a vulnerability and the potential impact (financial, reputational, regulatory) on the organization and patient safety.
Risk Determination & Control Recommendation: Calculate the overall risk level for each threat/vulnerability pair and then identify and recommend security controls to mitigate these risks to an acceptable level. This is where PCI DSS v4.0 requirements, HIPAA security rule provisions, and general best practices intersect.
Documentation and Review: Thoroughly document the TRA process and findings. Regularly review and update the TRA to reflect new threats, vulnerabilities, or changes in the mobile EHR environment.
Core Best Practices for Mobile EHR Security
Beyond PCI DSS v4.0 compliance, several core best practices are fundamental to significantly enhancing the security of your Secure Mobile EHR systems. Implement a Mobile Device Management (MDM) solution. It can enforce security policies, manage device configurations, remotely wipe lost/stolen devices, and control application installations. Ensure encryption for ePHI and any sensitive Data Security both at rest on mobile devices and in transit over networks. Mandate strong, unique passwords and enforce MFA for all access to mobile EHR systems.
Vet all mobile EHR applications and associated third-party apps for security vulnerabilities, implementing secure coding practices for in-house mobile applications, aligning with Application and DevOps Security principles. Utilize VPNs for remote access, secure Wi-Fi configurations (WPA2/3-Enterprise), and Network Security practices like network segmentation. Keep mobile device operating systems, EHR applications, and all related software up-to-date with the latest security patches. Educate clinicians and staff on secure mobile practices, phishing awareness, and incident reporting procedures through regular Awareness and Training. Develop and regularly test an incident response plan specifically addressing mobile security incidents.
Advanced and Forward-Looking Strategies for Fortifying Mobile EHR
To further mature your Secure Mobile EHR security posture and prepare for future challenges, consider implementing solutions for Continuous Monitoring of mobile devices and network traffic to detect and respond to threats in real-time. Subscribe to threat intelligence feeds to stay informed about emerging mobile threats and vulnerabilities relevant to healthcare.
Adopt an adaptive security architecture that can dynamically adjust to evolving threats and changing risk levels. Consider a Zero Trust model for your mobile environment, where no user or device is implicitly trusted, and access is granted on a least-privilege basis after strict verification. This is a key tenet for future-proofing your Secure Mobile EHR approach. These strategies help build a resilient defense against an ever-evolving threat landscape.
Conclusion: A Proactive Stance for Secure Mobile EHR
Undeniably, the migration to mobile EHR offers transformative potential for healthcare. However, to realize these benefits safely and effectively, organizations must prioritize the security of these systems. A proactive, risk-based approach, integrating comprehensive Threat Risk Assessments with the robust framework of PCI DSS v4.0, is crucial for establishing and maintaining a Secure Mobile EHR environment.
This journey requires diligence, ongoing assessment, and adaptation to new threats. Through understanding the risks, implementing best practices, and staying informed, healthcare organizations can then confidently embrace mobile technology, safeguard patient data, and continue to innovate in the delivery of care. Furthermore, establishing a strong security culture and leveraging appropriate technologies are key components of this ongoing commitment to protecting sensitive information in a mobile-first world.







