New Risk Analysis Methodology: A Strategic Framework
The Payment Card Industry Data Security Standard (PCI DSS) serves as a critical framework for protecting sensitive payment data. Adapting to the ever-changing threat landscape is essential. PCI DSS v4.0 emphasizes Targeted Risk Analyses (TRAs). This represents a significant evolution in safeguarding cardholder information. PCI DSS provides the overall structure for a secure payment processing system. In contrast, TRAs are the detailed evaluations. These evaluations ensure security measures are robust. They also ensure measures are appropriately tailored to withstand cyber threats. This article guides you on understanding and implementing TRAs. The goal is to achieve PCI DSS v4.0 compliance. It offers actionable strategies to protect your cardholder data environment.
The transition to PCI DSS v4.0 underscores a shift towards a more objectives-based approach to security. Previous versions were often seen as prescriptive. Version 4.0, however, encourages organizations to critically assess their specific risks and determine the best mitigation strategies. This involves more than just implementing controls. You must also understand why those controls are necessary. Additionally, grasp how they effectively reduce risk in your particular operational context. Mastering TRAs is central to this evolved approach, empowering organizations to build more resilient and adaptive security postures.This is particularly important because payment technologies and attack vectors continue to advance. This advancement requires a security framework that can keep pace.
What is a Targeted Risk Analysis (TRA) in PCI DSS v4.0?
A Targeted Risk Analysis (TRA) under PCI DSS v4.0 is a focused, precise evaluation. It assesses risks specific to an organization’s unique environment. It also addresses the particular PCI DSS requirements involved. This TRA moves beyond a general, broad-strokes risk assessment. Instead, it concentrates on how to implement or perform specific controls. It also considers the frequencies of activities related to PCI DSS requirements. TRAs are instrumental in two main scenarios. First, when an organization chooses a customized approach to meet a PCI DSS requirement. Second, when determining the appropriate frequency for certain security activities. This is especially true if the standard allows flexibility based on risk.
Fundamentally, a TRA helps answer critical questions. For instance: “How often should this security activity be performed to remain effective in our environment?” It also considers how controls should be implemented or customized. This must adequately mitigate identified risks for a requirement, given specific technologies and processes. This detailed thinking allows organizations to move away from a ‘one-size-fits-all’ mentality. TRAs mean businesses don’t rigidly apply every control in the same way. Instead, they optimize security practices based on documented risk assessments. This allows more effective resource allocation, providing robust data protection where it’s most needed. This enhanced flexibility, when supported by a rigorous risk analysis, can lead to stronger and more sustainable security. The process itself also fosters a deeper understanding within the organization of its threat landscape and the effectiveness of its security measures, contributing to a more mature security program.
Why are TRAs Important for PCI DSS v4.0?
PCI DSS v4.0 places a heightened emphasis on a risk-based approach to security. This shift reflects evolving cyber threats. It encourages organizations towards more proactive, strategic, and intelligent security. Organizations are no longer just meeting a requirement as written. The standard now often asks them to justify how they meet the requirement’s objective, particularly when customizing controls. The Verizon 2024 Data Breach Investigations Report (DBIR) consistently highlights that attackers frequently exploit known vulnerabilities that may not have been adequately addressed. TRAs help organizations focus their resources on the most significant threats and vulnerabilities pertinent to their cardholder data environment (CDE), enabling them to address weaknesses more effectively.
Specifically, performing TRAs in the context of PCI DSS v4.0 enables an organization to better prioritize its resources. Businesses should identify and analyze specific risks. This allows them to concentrate security efforts and investments on areas posing the greatest threat to their cardholder data. Such an approach avoids a uniform, and potentially less efficient, security strategy applied across the board. TRAs also provide flexibility. For certain PCI DSS v4.0 requirements, organizations can customize how they implement controls, provided they can demonstrate through a TRA that their customized approach meets the stated objective and rigor of the standard, and effectively mitigates the associated risks. This allows security measures to be better aligned with an organization’s specific operational processes and technological infrastructure. TRAs involve thoroughly analyzing risks and adapting controls accordingly. Ultimately, this contributes to an improved overall security posture. Such a posture helps reduce vulnerabilities and enhance protection against cyberattacks.
Key Requirements Involving TRAs in PCI DSS v4.0
While PCI DSS v4.0 is comprehensive, certain requirements specifically call for or are supported by TRAs. For instance, Requirement 12.3.1 mandates that organizations “Define the frequency of periodic reviews of security policies and procedures to ensure they remain relevant and effective.” A TRA would be used here to determine and justify an appropriate review frequency based on the organization’s risk environment. Similarly, Requirement 12.3.2 addresses the use of customized approaches. It states that for each customized control, the organization must take specific action. They must “Perform a targeted risk analysis for each customized control.” This analysis aims “to demonstrate how the customized control meets the stated PCI DSS requirement.” It must also show the control “provides at least the same level of security as the original requirement.” This involves documenting how the customized control implements protection and mitigates risks.
It’s important to understand: performing a Targeted Risk Analysis is not simply a formality. It is a mechanism. This mechanism empowers organizations. They can then implement enhanced, context-specific protection for cardholder data and maintain a more effective, resilient security posture. Organizations need to thoroughly review PCI DSS v4.0 to identify all instances where a TRA is required or can support compliance, particularly when deviating from a defined approach or determining frequencies of security activities. The outputs of these TRAs become critical evidence during a PCI DSS assessment.
Steps to Conduct a Successful Targeted Risk Analysis
Conducting a successful TRA for PCI DSS v4.0 compliance involves several key steps:
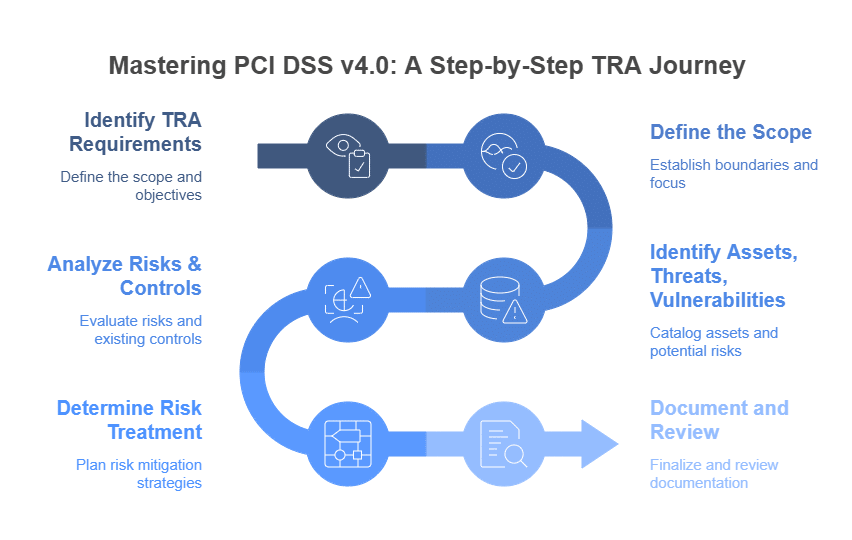
Identify PCI DSS Requirements Necessitating TRAs: Meticulously review the PCI DSS v4.0 standard to pinpoint all requirements that explicitly call for a TRA or where a TRA would be necessary to support a customized approach or define the frequency of an activity. The official PCI Security Standards Council (SSC) website is the definitive source for the standard.
Define the Scope of the TRA: Clearly determine which specific PCI DSS requirement, control, process, system, or environment the TRA will apply to. To keep the analysis focused and relevant, outline its boundaries and impact, considering all applicable data flows and system components.
Identify Assets, Threats, and Vulnerabilities: Within the defined scope, identify all critical assets involved (e.g., specific servers, applications, network devices processing or storing cardholder data). Then, identify potential threats. Examples include malware, unauthorized access, and system misconfiguration. Also, identify vulnerabilities like unpatched software, weak passwords, and insecure protocols. Both threats and vulnerabilities must be relevant to these assets and the specific PCI DSS requirement under review.
Analyze Risks and Existing Controls: Evaluate the likelihood of each identified threat exploiting a vulnerability and the potential impact on the confidentiality, integrity, or availability of cardholder data or the CDE. Assess the effectiveness of any existing controls in mitigating these risks. This analysis helps determine if current measures are sufficient or if the organization needs to make adjustments.
Determine and Document Risk Treatment: Based on the risk analysis, decide on the appropriate risk treatment. This could mean implementing new or modified controls. It might involve changing an activity’s frequency. Or, you could formally accept a risk, but only where permissible and documented with strong justification. Document the rationale for the chosen approach. You must detail how it meets the intent of the PCI DSS v4.0 requirement. Also, explain how it adequately mitigates the identified risks.
Document, Maintain, and Review the TRA: Thoroughly document the entire TRA process, including the scope, identified assets, threats, vulnerabilities, risk analysis, existing controls, decisions made, and justifications. This documentation is crucial for PCI DSS assessments. Establish a process to regularly review and update the TRA. This review and update is especially important. It should occur in response to significant changes in the environment, threat landscape, or PCI DSS requirements themselves.
Digging Deeper: Key Considerations for Each Stage
When identifying requirements, focus particularly on instances where customized approaches are being considered for meeting PCI DSS v4.0 objectives. In such cases, the TRA must rigorously document a key aspect. It must show how the tailored controls meet or exceed the original PCI DSS requirement. This includes addressing the requirement’s intent and rigor. Leverage resources from the PCI Security Standards Council (SSC). These resources include items like FAQs and guidance documents. They can aid in accurately interpreting and applying these requirements.
Defining the scope effectively requires accurate and up-to-date diagrams illustrating all relevant cardholder data flows. This helps visualize what systems and processes are in scope for the specific TRA. Reviewing and verifying network segmentation is also crucial, as proper segmentation can help minimize the scope of the CDE and, consequently, the scope of certain TRAs, thereby reducing risk.
For identifying assets and threats, maintaining a comprehensive and current inventory of all systems and components within the scope of the TRA is essential. This inventory should include details about the function of each asset and the data it handles. Employing threat modeling techniques can proactively identify potential threat vectors and attack scenarios relevant to the specific context of the TRA.
When analyzing vulnerabilities, it’s important to prioritize them based on the risk they pose, considering both the likelihood of exploitation and the potential impact. This allows security teams to focus remediation efforts efficiently. Develop clear remediation plans with defined steps, responsibilities, and timelines. These plans are necessary to ensure the organization effectively addresses identified vulnerabilities and implements or strengthens controls.
Determining TRA frequency, or the frequency of activities supported by a TRA, should consider the business impact of the systems or processes involved, ensuring assessments align with operational needs and minimize disruption. The approach should be dynamic; the frequency of reviews or activities may need adjustment based on the findings of previous TRAs, changes in the threat landscape, or significant modifications to the environment.
Finally, comprehensive documentation and maintenance are paramount. Using risk registers to log each component of the analysis, including identified risks, controls, and treatment decisions, ensures proper tracking and provides a clear audit trail. Controls and TRAs themselves should be reviewed regularly, and especially when key changes occur in IT systems, business processes, or the threat environment, to ensure they remain effective and aligned with PCI DSS v4.0.
Best Practices for Implementing and Performing TRAs
To ensure TRAs are effective and contribute meaningfully to PCI DSS v4.0 compliance and overall security, organizations should adhere to several best practices. Prioritizing thorough documentation is essential. Maintain detailed records of TRA procedures, the data and inputs used, the analysis performed, results, decisions made, and justifications. This comprehensive record not only facilitates a smoother assessment process but also ensures that future TRA efforts are consistent and build upon previous work.
Integrating current threat intelligence from reputable sources is crucial. This helps organizations stay informed about emerging threats, new attack vectors, and evolving adversary tactics and techniques relevant to their industry and technology stack. A proactive approach, informed by threat intelligence, enables security operations teams to anticipate and respond more effectively to potential vulnerabilities.
Engaging key stakeholders from various departments—such as IT, Security, Compliance, Legal, and relevant business units—is also a vital best practice. This collaborative approach fosters a broader understanding of risks across the organization, helps ensure that security strategies align with business objectives and operational realities, and promotes shared responsibility for security. Leveraging automation where appropriate can streamline certain aspects of the TRA process, such as data collection or vulnerability scanning, improving efficiency and consistency.
Common Challenges and How to Overcome Them
Implementing TRAs effectively can present challenges. A lack of in-house expertise in risk analysis or specific PCI DSS v4.0 nuances is common. Organizations can address this by investing in training for their staff, engaging external PCI DSS experts or Qualified Security Assessors (QSAs) for guidance, or utilizing industry-standard risk management frameworks.
Keeping up with the rapid pace of change in technology, the threat landscape, and PCI DSS itself is another significant challenge. This requires organizations to be adaptable and commit to regular reviews and updates of their TRAs and associated security controls. TRAs should not be a one-time exercise but an ongoing process. Integration difficulties can also arise if you treat TRAs as isolated activities. To overcome this, integrate TRAs into your organization’s overall risk management program and system development lifecycle. This approach fosters a more holistic and proactive security posture.
The Role of Technology and Automation
Leveraging appropriate technology and automation can significantly enhance the efficiency and effectiveness of managing Targeted Risk Analyses for PCI DSS v4.0. Vulnerability scanning tools can automate the detection of technical vulnerabilities, helping security analysts identify and prioritize risks more effectively. Security Information and Event Management (SIEM) solutions centralize security logs and event information, providing a clearer view of the security landscape and supporting the analysis required for TRAs, particularly in assessing the effectiveness of existing controls.
Risk management platforms can streamline the overall risk analysis process, manage compliance documentation, and provide an integrated view of an organization’s risk posture. These platforms can help manage the workflow of TRAs, track remediation efforts, and maintain an audit trail. By integrating these tools, organizations can create a more holistic and partially automated approach to TRAs, allowing for more efficient tracking, consistent application of methodologies, and quicker response to identified issues.
Future-Proofing Your PCI DSS Compliance
Maintaining PCI DSS v4.0 compliance and a strong security posture in the long term requires a proactive and adaptive strategy. Organizations must continuously evolve their security practices to respond to changes in their business, technology, and the threat environment. This means not viewing compliance as a static, point-in-time achievement but as an ongoing program of continuous improvement.
Investing in regular Awareness and Training for personnel is crucial to ensure they are up-to-date with current regulations, security policies, and emerging threats. Engaging with industry peers, security forums, and expert partners can also provide valuable insights and help keep PCI DSS compliance efforts at the cutting edge. Furthermore, exploring the appropriate use of emerging technologies, such as AI and machine learning for advanced threat detection or streamlining compliance tasks, can help organizations enhance their security capabilities and adapt to future challenges more effectively.
Conclusion
Targeted Risk Analyses are a vital component for organizations seeking to maintain PCI DSS v4.0 compliance and robust security operations. By understanding the purpose of TRAs, following a structured approach to conduct them, and adhering to best practices, businesses can effectively identify and mitigate risks specific to their environment, protect valuable cardholder data, and foster a pervasive culture of cybersecurity awareness and diligence. Remember, compliance is not merely about checking boxes; it is a continuous, strategic process that, when implemented effectively, can yield tangible business benefits by enhancing security, building trust, and protecting the organization’s reputation.







