From Perceived Isolation to Real-World Exposure
The convergence of Information Technology (IT) and Operational Technology (OT) has dramatically altered the security landscape for industrial environments. What was once a relatively isolated world of ICS is now increasingly connected. This brings new efficiencies. However, it also introduces significant vulnerabilities. Recent analysis reveals a concerning reality: a substantial number of Exposed OT and SCADA (Supervisory Control and Data Acquisition) devices are connected to the public internet, creating a vast and vulnerable attack surface that requires urgent attention.
For decades, the concept of an “air gap”—a physical or logical separation between OT and IT networks—provided a degree of security assurance. However, the practical reality is that this gap has significantly eroded or, in many cases, become a misconception. The drive for operational efficiency, remote monitoring, and data analytics for process optimization is strong. This has led to numerous digital interconnections between these once-separate domains. Consequently, attackers may no longer need to overcome physical barriers to access industrial systems. Inadequately secured digital pathways can provide direct access. This article delves into the data behind the threat to Exposed OT, explains why traditional IT security approaches are often insufficient for OT environments, and provides a strategic framework for defending the critical systems that underpin modern society.
The Alarming Reality: What the Data on Exposed OT Reveals
The threat to Exposed OT systems is not merely theoretical; it is a quantified and growing concern. Collaborative research from Palo Alto Networks and Siemens was highlighted in a report. It identified over 1.25 million SCADA and OT devices exposed to the internet. This exposure is not a passive risk. For instance, FortiGuard Labs, in their threat landscape reports, have recorded billions of exploitation attempts annually. As a result, reconnaissance efforts targeting industrial systems are surging globally. Cybercriminals and other threat actors are now deploying automated scanning techniques at an unprecedented scale—some estimates equate this to tens of thousands of scans per second—to map these Exposed OT systems and identify vulnerable targets, often before patches or mitigations can be applied.
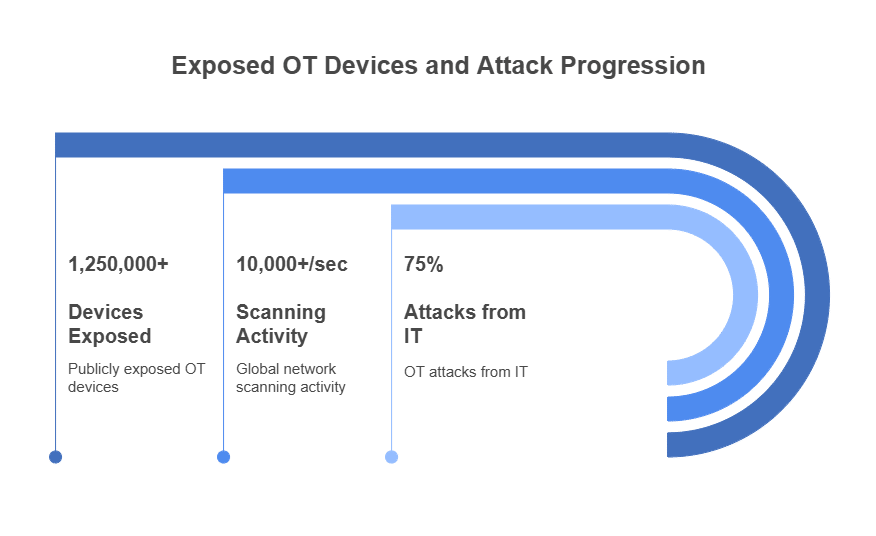
This relentless scanning creates what is often referred to as a ‘digital shadow’ of our critical infrastructure. This shadow provides adversaries with a detailed blueprint of vital systems, including their potential vulnerabilities and interconnections. Therefore, the question for organizations managing OT environments is no longer if they will be targeted, but when and how effectively they can defend against such attacks. The sheer volume of exposed devices underscores the scale of the challenge. It also highlights the urgent need for robust security measures specifically designed for OT environments.
Why Traditional IT Security Fails in the OT World
Applying IT security frameworks directly to OT environments is often flawed because IT and OT systems have vastly different core priorities. IT security typically prioritizes data protection (Confidentiality, Integrity, Availability), with the primary goal often being data safeguarding. In contrast, OT security emphasizes the safe, reliable, and continuous operation of physical processes, prioritizing Safety, Control, and Availability. Consequently, disruption impacts vary significantly. An IT issue might cause minor inconvenience or a slow webpage. In contrast, an OT failure, like a delayed command, could lead to catastrophic physical events. Examples include blackouts, chemical plant incidents, or other severe consequences.
This fundamental difference creates critical challenges where IT-centric security falls short, especially with OT equipment lifecycles often spanning 15-30 years, unlike IT’s typical 3-5 year refresh. This results in OT environments with legacy hardware and outdated, unsupported software. For example, a 2024 Palo Alto Networks report showed many OT exploits (61.9%) target 6-10 year old vulnerabilities. These are often called ‘foreverdays.’ These flaws in legacy systems are unlikely to be patched. Reasons include operational constraints, lack of vendor support, or disruption risk. Standard IT patch management, with its frequent schedules, is often impractical and potentially dangerous in OT, potentially causing more harm than the vulnerability itself. Thus, OT necessitates a more nuanced, risk-based approach to vulnerability management.
The Modern Threat Landscape for Exposed OT
As OT systems increasingly connect to IT networks and the internet, attack vectors multiply, with sophisticated attackers targeting unique vulnerabilities in converged IT/OT environments. Ransomware, once an IT problem, now significantly threatens industrial operations. Threat actors, recognizing OT’s high disruption potential, increasingly target these sectors. A 2023 Dragos report (published early 2024) showed a substantial rise in ransomware attacks on industrial organizations, especially manufacturing. The motivation is clear. OT downtime means massive financial loss, supply chain disruption, and potential safety incidents, pressuring victims to pay. These attacks often exploit weaknesses for initial entry. Examples include insecure remote access or unpatched internet-facing systems, allowing lateral movement into the core OT network.
Lateral movement from IT to OT networks critically challenges the ‘air gap’ defense. Research (e.g., Telstra, Omdia) indicates a large majority of OT cyberattacks (around 75%) originate within the IT network. Adversaries might compromise a corporate system via phishing, then pivot across the network, find a poorly secured IT/OT connection or shared credential, and ultimately control physical processes. This highlights failures in network segmentation and access control between domains. A single IT weakness or compromised account can lead to catastrophic OT failure, underscoring the urgent need for a holistic, layered, defense-in-depth security strategy encompassing both IT and OT with proper segregation and controls.
A Proactive Defense: Strategic Framework for Securing Exposed OT
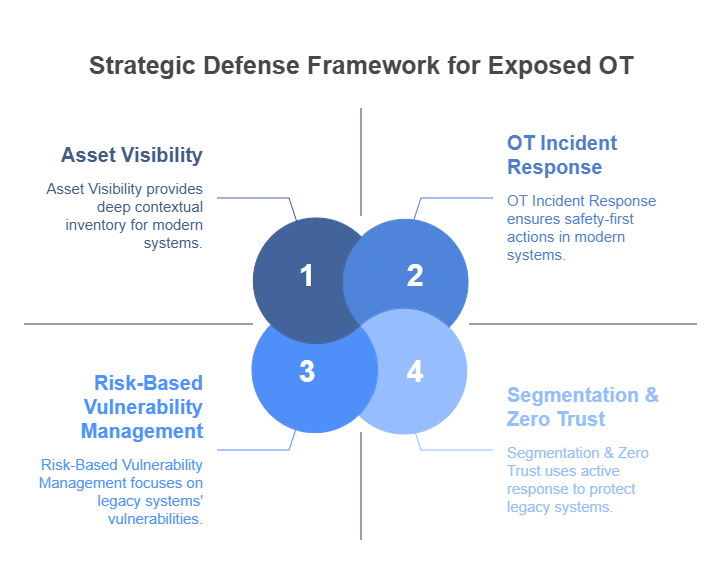
Protecting Exposed OT systems requires a strategic shift from a primarily reactive, perimeter-based defense model to a proactive, risk-based strategy that emphasizes visibility, segmentation, tailored vulnerability management, and robust incident response capabilities. Here is a practical, four-step strategic framework for CISOs and security leaders:
Achieve Comprehensive Asset Visibility: Organizations cannot effectively protect what they cannot see. The foundational step is to create and maintain a comprehensive Asset Inventory and Management of every device within the OT environment. This inventory must go beyond a simple list of IP addresses. It requires a deep understanding of each asset. This includes its function, communication patterns, software/firmware versions, and criticality to the overall industrial process. Due to the sensitive nature of OT equipment, passive network monitoring and specialized OT visibility tools are essential, as active scanning techniques common in IT can disrupt or damage sensitive industrial processes.
Implement Robust Network Segmentation and Zero Trust Principles: Once visibility is established, organizations can begin to implement or enhance network segmentation. The goal is to create logical zones, often guided by models like the Purdue Enterprise Reference Architecture. These zones isolate critical control systems from corporate networks and, especially, from direct internet exposure. This involves using firewalls, unidirectional gateways, and demilitarized zones (DMZs) to create controlled chokepoints where security systems/organizations can inspect and strictly regulate traffic. A Zero Trust mindset is crucial: systems/the architecture should not trust any communication by default, regardless of its origin. Every connection between the IT and OT worlds, and even between segments within the OT environment, requires systems/security mechanisms to authenticate, authorize, and log it. Implementing strong Network Security is paramount.
Adopt Risk-Based Vulnerability Management: The “patch everything immediately” mentality common in IT environments is often unworkable and potentially hazardous in OT. Given the prevalence of legacy systems and “foreverdays,” a risk-based approach to Posture and Vulnerability Management is essential. Therefore, frameworks and methodologies that help prioritize vulnerabilities based on their potential impact on safety and operations, their exploitability in the specific OT context, and the presence of active threats are more effective. This allows security teams to focus their limited resources on addressing vulnerabilities posing the most significant actual risk to operations. They should not attempt to remediate every identified Common Vulnerability and Exposure (CVE).
Develop and Test an OT-Specific Incident Response Plan: An Incident Response plan tailored for OT environments is fundamentally different from a typical IT IR plan. According to entities like the SANS Institute, a surprisingly low percentage of industrial facilities have a documented, tested, and up-to-date IR plan specifically for OT incidents. An OT IR plan has key characteristics. Engineering and operations personnel must lead it. Safety is the top priority. It must include clear, pre-defined procedures. Examples are moving to manual operations, isolating affected systems, or executing a safe, orderly process shutdown. Regular tabletop exercises and simulations are non-negotiable. These must be based on realistic OT-centric scenarios. Examples are a ransomware attack on an HMI for a critical process, or a PLC compromise. Their purpose is to ensure the plan’s effectiveness and team preparedness.
Conclusion: From Vulnerable to Resilient
The digital transformation of industry has brought incredible benefits in efficiency and operational insight, but it has also left some of our most critical infrastructure dangerously exposed if not managed correctly. The data clearly indicates that Exposed OT is a widespread, actively targeted, and high-stakes problem. Relying on outdated security paradigms like the presumed “air gap” is no longer a viable or realistic strategy.
Securing the modern industrial landscape requires a fundamental shift in mindset and approach. Therefore, it demands several actions from organizations. The primary action is that they must break down traditional cultural and technical silos between IT and OT security teams. Second, they need to foster a culture of shared responsibility for securing industrial operations. Third, they should adopt a comprehensive security framework. This framework must prioritize safety, operational resilience, and proactive risk management. Organizations relying on industrial processes have a core business.
This business intrinsically depends on the integrity and availability of their Industrial Control Systems (ICS). For this reason, protecting these systems is not just a technical IT requirement; rather, it is essential for ensuring economic stability, national security, and public safety. By implementing robust visibility, segmentation, risk-based vulnerability management, and OT-specific incident response capabilities, organizations can move from a state of vulnerability to one of enhanced resilience.







