Cybersecurity Crises and Federal Mandates: The Intersection
The cybersecurity landscape has dramatically shifted. This greatly impacts those in healthcare operations or patient care. It also affects anyone managing electronic Protected Health Information (ePHI), with ransomware being a key concern. Once a lesser concern, ransomware now represents a significant and ongoing crisis-level threat, with sophisticated cybercriminals persistently targeting healthcare organizations. The threat of ransomware is increasing in frequency. The severity of its impact is also growing. Additionally, the intensity of regulatory scrutiny is rising. Consequently, understanding and implementing a Ransomware & HIPAA-compliant response is no longer a matter that can be postponed; it is absolutely critical for safeguarding patient care, ensuring data privacy, and maintaining organizational stability.
Guidance from the Department of Health and Human Services (HHS) and the relentless wave of healthcare breaches paint a stark reality. Ransomware adversaries often operate with alarming speed and effectiveness, exploiting vulnerabilities to encrypt data and disrupt essential services. These attackers leverage readily available tools and sophisticated social engineering tactics. These tactics can erode traditional defenses. This makes a robust, HIPAA-aligned response more critical than ever. This is not merely a digital disruption; attackers directly impact patient safety by crippling access to medical records, diagnostic systems, and treatment plans.
This trend underscores the growing severity of the ransomware threat to healthcare. Insights from HHS Office for Civil Rights (OCR) enforcement actions reinforce this alarming trend. Cybersecurity frameworks also support this view. One such framework is NIST SP 800-66r2. Its full title is “An Introductory Resource Guide for Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule.” Threat intelligence reports also confirm this. Notable examples are the ENISA Threat Landscape and the Verizon DBIR. These reports highlight two key issues. First, the increasing complexity of attacks. Second, the urgent need to address a dual challenge head-on. This challenge involves ransomware recovery and stringent Ransomware & HIPAA compliance.
So, what do HHS guidance and these persistent attacks tell us about achieving a compliant response? What does this mean for your healthcare organization’s preparedness and operational resilience?
The Core Challenge: Ransomware’s Mechanics and HIPAA’s Demands
HHS OCR guidance and the nature of ransomware attacks emphasize a critical point. Under HIPAA, these incidents are presumed to be breaches. Therefore, healthcare organizations must take immediate and meticulous HIPAA-compliant actions. This dual pressure from attackers and regulators stems from several key factors:
The operational model of ransomware involves attackers deploying malicious software. This software encrypts an organization’s data, rendering systems and vital ePHI inaccessible. They then demand a substantial ransom, typically in cryptocurrency, for a decryption key. Healthcare organizations are particularly attractive targets due to their critical reliance on immediate access to patient data, the sensitive nature of ePHI, and, in some instances, perceived vulnerabilities in their IT infrastructure.
The impacts of such attacks are widespread and devastating, extending far beyond financial loss to directly affect patient safety. Disrupted access to medical records, imaging systems, and treatment plans can delay or compromise care, potentially leading to adverse health outcomes. Furthermore, any unauthorized access to or disclosure of ePHI during an attack constitutes a security incident under HIPAA. In most cases, this is also a reportable breach. This is particularly true if ePHI is encrypted or exfiltrated. This incurs significant costs from recovery efforts, legal fees, regulatory fines, and patient notifications, alongside severe reputational damage that erodes patient trust.
HIPAA’s strict presumption regarding breaches is a central challenge. HHS OCR guidance clearly states that when ransomware affects a Covered Entity’s or Business Associate’s systems, it is a HIPAA security incident. Critically, if ransomware encrypts ePHI, HIPAA presumes a breach has occurred. An organization can only rebut this presumption. To do so, they must use a thorough and documented risk assessment. This assessment must demonstrate a low probability of PHI compromise. This assessment must consider multiple elements. It must consider the nature and extent of the PHI involved. It should also identify the unauthorized person who used the PHI or to whom the disclosure was made. Furthermore, it must determine if the PHI was actually acquired or viewed. Lastly, it must assess the extent to which the risk to the PHI has been mitigated.
Key HIPAA Mandates and Pre-Incident Vulnerabilities
Successful ransomware attacks often correlate with unaddressed vulnerabilities and gaps in preemptive HIPAA-mandated security measures. Attackers systematically exploit weaknesses that organizations should have identified and mitigated through diligent adherence to the HIPAA Security Rule. The Security Rule itself points to foundational areas where lapses can invite such incidents, making proactive compliance a critical defense.
HIPAA’s Security Rule mandates thorough Risk Analysis and Risk Management (§ 164.308(a)(1)(ii)(A) and (B)). This mandate highlights a primary area where vulnerabilities often originate. Covered Entities and Business Associates must conduct accurate and thorough assessments of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI. They must also implement security measures sufficient to reduce those risks and vulnerabilities to a reasonable and appropriate level. Failure in this foundational step of ongoing risk management frequently precedes successful ransomware attacks. HHS guidance and OCR investigations will scrutinize an organization’s pre-incident risk management activities closely.
Unaddressed vulnerabilities serve as critical entry points. The most recent ENISA Threat Landscape often details several issues. (This refers to the 2023 report, assuming current findings). Examples include unpatched software, weak access controls, or insufficient employee training. If these issues are missed or inadequately addressed during risk analyses, they pose significant threats. NIST SP 800-66r2 guidance on HIPAA security emphasizes foundational risk identification and remediation. Yet, many organizations struggle with comprehensive and timely patching, often due to operational constraints, legacy systems, or a lack of awareness regarding the criticality of certain patches. This leaves ePHI dangerously exposed.
Insufficient employee training is another prevalent entry vector. Staff may be unable to recognize or appropriately report phishing attempts or other suspicious activity. This can inadvertently allow adversaries to succeed with relatively simple social engineering techniques. This reinforces that failures in basic cyber hygiene related to human factors significantly contribute to ransomware incidents, making staff the first, and sometimes weakest, line of defense.
The Incident Unfolds: HIPAA’s Scrutiny on Response and Recovery
Once an organization detects a ransomware attack, its ability to execute its incident response plan under pressure is severely tested, and its adherence to HIPAA requirements comes under intense scrutiny from HHS. HHS will meticulously review the organization’s preparedness and the effectiveness of its security incident response procedures. The focus shifts to how well the entity identifies, responds to, mitigates, and documents the security incident in accordance with HIPAA’s Security Incident Procedures (§ 164.308(a)(6)). This process often reveals gaps. These gaps are not necessarily in the attacker’s sophistication. Instead, they are in the organization’s detection capabilities, containment strategies, or overall response coordination.
The Contingency Plan (§ 164.308(a)(7)) becomes paramount, and its comprehensiveness and diligent execution are vital. This plan requires specific components. These include data backup plans, disaster recovery plans, and emergency mode operation plans. All are designed to ensure the availability and integrity of ePHI during and after an emergency. Organizations must have robust, frequently tested backups that are encrypted, stored offline or in a logically segregated environment, and ideally immutable. Well-rehearsed recovery processes are also essential. Failures in these areas can lead to prolonged disruption of patient care. They can also cause an inability to restore ePHI integrity and significant operational paralysis. Such failures directly contravene HIPAA mandates. They also catastrophically worsen the incident’s impact and potential penalties.
Broader Compliance Considerations: Notifications and Documentation
The scope of Ransomware & HIPAA compliance expands significantly post-incident, particularly concerning the complex and time-sensitive requirements of the Breach Notification Rule (45 C.F.R. §§ 164.400-414). Organizations must meticulously assess if a breach of unsecured PHI occurred. If so, they must notify affected individuals without unreasonable delay, and in no case later than 60 calendar days following the discovery of the breach. They must also notify HHS; for breaches affecting 500 or more individuals, this notification is concurrent with individual notifications. For smaller breaches (affecting fewer than 500 individuals), HHS is notified annually. Additionally, for larger breaches impacting over 500 residents of a particular state or jurisdiction, prominent media outlets serving that area must also be informed.
Meticulous documentation of every step taken in response to the incident is absolutely crucial. This documentation should cover everything from initial detection through investigation, containment, eradication, recovery, the post-incident risk assessment, and final remediation efforts. HHS HIPAA Security Series papers consistently emphasize the importance of such documentation for demonstrating HIPAA compliance to OCR. This documentation must include the formal breach risk assessment. This assessment rigorously applies the four-factor analysis. The goal is to determine if a reportable breach of unsecured PHI occurred. The analysis considers several factors. These include the nature and extent of PHI involved and the unauthorized person. It also considers whether PHI was actually acquired/viewed and the extent of mitigation. Reporting the crime to law enforcement agencies, such as the FBI or the Secret Service, is also a key step; however, these agencies might request a delay in public notification if it could impede their investigation.
Crafting an HHS-Compliant HIPAA Ransomware Response Plan: Practical Steps
Navigating a ransomware incident successfully demands a shift from reactive crisis management to proactive, Ransomware & HIPAA-aligned preparation. This preparation builds on thorough risk management, robust controls, and well-tested incident response capabilities. Here are key, actionable recommendations derived from HHS guidance and industry best practices:
Conduct Regular and Thorough Risk Analyses: Identify all systems, applications, and assets that create, receive, maintain, or transmit ePHI. Assess vulnerabilities that ransomware could exploit, such as unpatched software, weak credentials, misconfigured access controls, or insufficient employee training. NIST SP 800-66r2 guidance emphasizes this as foundational. Actionable Step: Engage in periodic, comprehensive HIPAA Security Risk Assessments that specifically evaluate ransomware threats to uncover and prioritize the remediation of ePHI vulnerabilities.
Implement Robust Security Measures: Based on the findings of your risk analysis, implement and maintain the administrative, physical, and technical safeguards required by the HIPAA Security Rule. This includes strong Identity Management and Access Control (applying principles like least privilege), Audit Controls (recording and examining system activity), Integrity Controls (preventing improper alteration or destruction of ePHI), and Transmission Security (encrypting ePHI in transit and at rest where appropriate). Deploy modern Endpoint and Device Protection solutions, such as Endpoint Detection and Response (EDR), and ensure rigorous Patch Management processes are in place. The most recent ENISA Threat Landscape notes unpatched vulnerabilities as a major attack vector.
Develop and Test a Comprehensive Contingency Plan: This plan is critical for your Ransomware & HIPAA response. It must include a Data Backup Plan (regularly back up ePHI, encrypt backups, store them offline or segregated, make them immutable if possible, and test restoration frequently), a Disaster Recovery Plan for restoring systems and ePHI, and an Emergency Mode Operation Plan establishing procedures for critical operations during an emergency. Actionable Step: Regularly schedule and execute backup restoration tests and conduct full tabletop exercises or functional drills of your entire contingency plan with all relevant stakeholders.
Develop a Written Security Incident Procedures & Enhance Awareness: Your Security Incident Response Plan (SIPP) must detail clear procedures for Detection and Analysis, Containment, Eradication, Recovery, and Post-Incident Activity (including lessons learned and plan updates). Crucially, train all workforce members on recognizing phishing, malware protection, safe computing practices, and their specific roles and responsibilities during an incident. Actionable Step: Implement ongoing, role-based Awareness and Training, incorporate ransomware-specific scenarios, and conduct regular tabletop exercises to test and refine your SIPP.
Execute During-Incident Procedures Diligently: Upon suspecting or confirming a ransomware attack, immediately activate the SIPP. Focus on containment by isolating affected systems to prevent the spread of malware. Preserve forensic evidence (system logs, malware samples) for investigation and for law enforcement. Once contained, safely eradicate the malware, which may involve using anti-malware tools or rebuilding affected systems from trusted sources. Consult with cybersecurity experts, HIPAA legal counsel, and cyber insurers as pre-planned. Actionable Step: Establish retainers or pre-vetted contacts for external Incident Response forensics teams and experienced HIPAA legal counsel before an incident occurs.
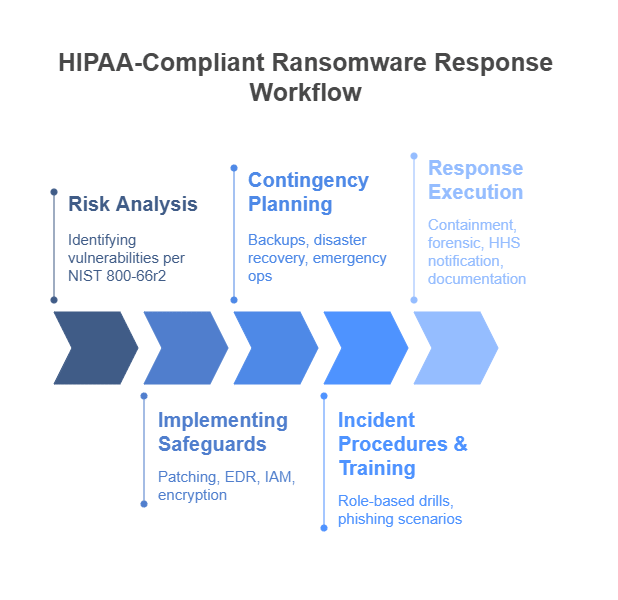
Following containment and eradication, restore ePHI and systems from clean backups, prioritizing critical patient care systems. Conduct a thorough post-incident analysis to determine the scope of the breach (all ePHI potentially affected), analyze the attack vector, assess the effectiveness of the response, and identify lessons learned. Based on these findings, update security policies, procedures, and contingency plans; continuous improvement is vital, as highlighted in the Verizon DBIR (assuming the 2025 version would continue this trend, or the latest available version). Perform the mandatory Breach Risk Assessment per HHS guidance and meet all Breach Notification Rule obligations. Throughout this entire process, meticulously document everything.
Conclusion: Proactive Compliance is Your Best Defense
HHS guidance and the persistent ransomware threat paint a clear, urgent picture: healthcare organizations face a constant challenge from sophisticated adversaries. A ransomware attack severely tests any healthcare organization’s resilience, and a failure in the Ransomware & HIPAA response can be as damaging as, if not more so than, the attack’s initial operational impact. Complacency is not an option when patient safety and sensitive data are at stake.
Organizations must adopt a proactive, adaptive security posture that moves beyond mere recovery to ensure comprehensive HIPAA compliance throughout an incident. By focusing on ongoing risk analysis, implementing robust controls, and meticulously fulfilling all post-incident obligations, including breach risk assessment and notification, leadership and security teams can build true resilience.







