AI in NERC CIP Vulnerability Management: Assessing Viability
Individuals immersed in Bulk Power System (BPS) operations understand a key fact. The North American Electric Reliability Corporation’s Critical Infrastructure Protection (NERC CIP) standards form the cybersecurity foundation. As energy infrastructure grows increasingly interconnected and reliant on complex software, managing NERC CIP SBOM vulnerabilities has undeniably emerged as a paramount challenge. Software Bills of Materials (SBOMs) are essential for understanding the components within software. Yet, the sheer volume and dynamic nature of these components create significant issues, transforming vulnerability management into an demanding task. Consequently, organizations are keenly looking towards advanced technologies. This article explores whether Artificial Intelligence (AI) tools, exemplified by platforms like Wiz, can indeed provide effective solutions to these pressing cybersecurity concerns related to NERC CIP SBOM vulnerabilities.
The evolution of these challenges within critical infrastructure presents a complex picture, particularly regarding software supply chain intricacy. The journey to robust management of NERC CIP SBOM vulnerabilities is difficult, as traditional, manual approaches to tracking software components and their associated vulnerabilities are rapidly becoming untenable. The primary issue isn’t necessarily that adversaries are becoming “stealthier”; rather, the sheer scale of potential vulnerabilities exposed through detailed SBOMs provides a vastly expanded attack surface if not managed proactively. The allure of AI-driven automation is therefore strong, promising speed, scale, and accuracy in sifting through this voluminous data.
This trend underscores the growing severity of software supply chain risks. Insights from NERC CIP standards themselves, particularly CIP-013 (Supply Chain Risk Management), CIP-010 (Configuration Change Management and Vulnerability Assessments), and CIP-007 (Systems Security Management), all reinforce this concern by placing significant emphasis on understanding and mitigating risks associated with software. Collectively, they highlight the increasing complexity and the urgent need to address the landscape of NERC CIP SBOM vulnerabilities head-on. Without a clear understanding of software components, identifying and addressing these vulnerabilities becomes a high-stakes endeavor.
So, what exactly are these standards and the nature of SBOMs telling us about how AI tools might offer an advantage, and what does it mean for BPS operations managing NERC CIP SBOM vulnerabilities?
AI’s New Edge: Automation and Insight in Addressing NERC CIP SBOM Vulnerabilities
The NERC CIP compliance landscape emphasizes that managing SBOM data effectively requires new capabilities, and Artificial Intelligence offers a promising avenue. This potential acceleration in addressing NERC CIP SBOM vulnerabilities is driven by several key capabilities AI brings to the table. AI can assist in parsing various software package formats to generate or ingest SBOMs. It then automatically analyzes them for known vulnerabilities by cross-referencing extensive databases like the Common Vulnerabilities and Exposures (CVE) list and the National Vulnerability Database (NVD). This includes continuously monitoring software components for newly disclosed vulnerabilities, providing timely alerts to security teams.
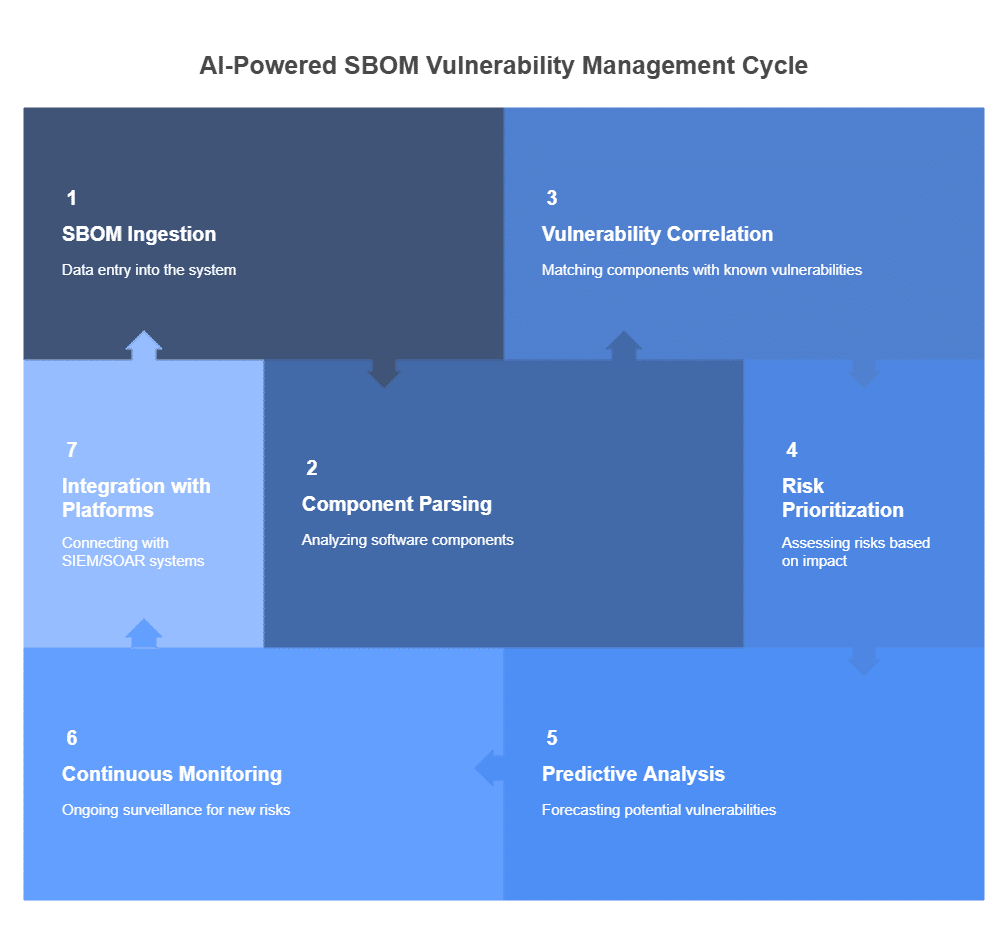
Furthermore, AI algorithms can help prioritize identified vulnerabilities. These systems assess factors such as exploitability, potential impact on Bulk Electric System (BES) Cyber Systems (especially when integrated with asset context from platforms like Wiz), and the presence of mitigating controls. This allows teams to focus their limited resources on the most critical risks related to NERC CIP SBOM vulnerabilities. Advanced AI models are also being developed with the potential to predict which software components are likely to become vulnerable in the future. By analyzing historical data, code complexity, and development practices, AI could offer valuable foresight into emerging threats within the software supply chain, further aiding in proactive management.
The SBOM Data Challenge in the NERC CIP Context
The increase in software complexity confirms a pronounced emphasis on component tracking within the NERC CIP SBOM vulnerabilities landscape. However, the scale is daunting. Modern software applications can contain thousands of individual components, many being open-source or third-party libraries. Yet, despite its significant potential, AI is not a panacea. Its effectiveness in managing NERC CIP SBOM vulnerabilities depends heavily on the quality and completeness of input SBOMs and the accuracy of vulnerability feeds. Human oversight remains critical, especially in the high-stakes environment of critical infrastructure, to validate AI findings and make informed risk decisions.
Understanding why SBOMs are critical for NERC CIP compliance is key. SBOMs offer unprecedented visibility into the software supply chain, revealing all third-party and open-source components that might otherwise hide NERC CIP SBOM vulnerabilities. By mapping these components against known vulnerability databases, organizations can more quickly identify software susceptible to exploitation. This detailed understanding allows for a more accurate risk assessment regarding the potential impact on BES Cyber Systems. It also serves as crucial compliance evidence for various NERC CIP requirements. This is particularly true for those requirements related to vulnerability management and supply chain risk.
The operational landscape is also evolving. Cloud services are increasingly used for several key functions. These include data analytics, management interfaces, and even some control system functions. This trend is especially noticeable in modernized substations. It also applies to enterprise IT systems that interact with Operational Technology (OT). Tools like Wiz, which lead in cloud security posture management (CSPM) and cloud workload protection (CWPP), can therefore play a significant role. They assist in securing these cloud and cloud-connected components, contributing to the overall management of NERC CIP SBOM vulnerabilities for those assets that fall within or support the NERC CIP scope.
AI’s Operational Integration for Cloud-Based NERC CIP Assets
Once cloud-based assets are in NERC CIP scope, AI-driven tools like Wiz prioritize a specific analysis. This analysis is comprehensive, deeply integrated with cloud fabrics, and provides continuous visibility. Wiz’s capabilities demonstrate this deep integration by providing a comprehensive cloud asset inventory. This inventory is foundational, helping organizations understand where software with potential NERC CIP SBOM vulnerabilities is running within their cloud footprint. Furthermore, it scans cloud workloads for known vulnerabilities present in operating systems, applications, and libraries. This process directly addresses the need to identify vulnerabilities for cloud-hosted assets, such as SCADA management servers or data historians that might support BES operations.
Wiz’s risk-based prioritization helps teams focus on critical cloud vulnerabilities by considering factors like exposure, permissions, and potential impact. It also offers insights into risky software packages and misconfigurations in cloud-native development pipelines. This helps secure the supply chain of cloud applications. These applications interact with NERC CIP-relevant systems. This comprehensive view is essential for managing the attack surface associated with NERC CIP SBOM vulnerabilities in hybrid environments.
Expanding Scope: Cloud Footprints and Supply Chain Scrutiny
Integrating cloud services into BPS-supporting architecture inevitably expands the attack surface. NERC CIP standards implicitly address this concern through requirements for rigorous risk management. Platforms like Wiz observe how attackers target cloud environments by exploiting persistent weaknesses, such as misconfigurations or unpatched software. For NERC CIP entities, this means they must scrutinize any cloud component interacting with or supporting BES Cyber Systems for NERC CIP SBOM vulnerabilities with the same diligence applied to on-premises systems. This diligence includes understanding the software composition of these cloud services.
Supply chain risks are a core focus of NERC CIP-013. These risks are amplified in the highly interconnected software ecosystem where components are sourced from numerous vendors and open-source projects. AI tools can assist in parsing SBOMs to identify components with known issues or from untrusted sources. NERC documentation highlights the complexity of vendor and subcontractor relationships. This complexity can create opportunities for malicious code or vulnerabilities to be introduced into the supply chain. This growing vector for NERC CIP SBOM vulnerabilities demands a rigorous approach to third-party software risk management. Such an approach ensures that SBOMs are obtained and analyzed, potentially with AI assistance, and that these SBOMs are continuously monitored throughout the software lifecycle. This monitoring is especially critical for components vital to BPS reliability.
Practical Defenses: Addressing NERC CIP SBOM Vulnerabilities
Navigating the complexities of NERC CIP SBOM vulnerabilities demands a shift from purely reactive patching to proactive risk management. This strategy should be built on visibility, control, and resilience, where AI can serve as a powerful ally. Here are key, actionable recommendations:
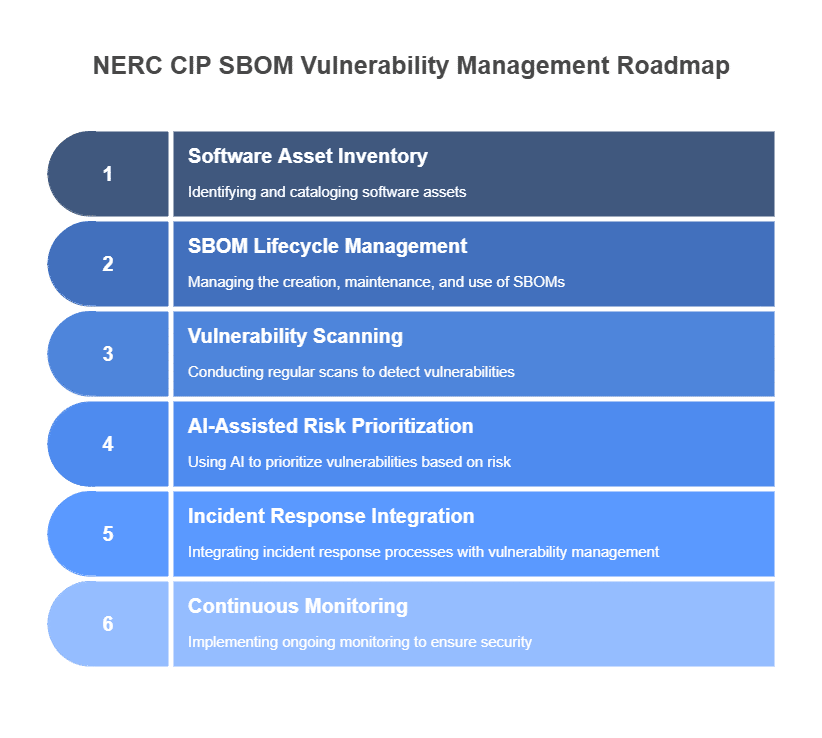
Establish a Comprehensive Asset Inventory: An organization cannot protect what it does not know, and this includes software assets. An accurate SBOM for critical software is the starting point. Actionable Step: Implement processes and tools, potentially AI-assisted, for generating or ingesting and maintaining SBOMs for all in-scope BES Cyber Systems and their supporting elements. Ensure this Asset Inventory and Management is regularly updated.
Define Clear Policies and Procedures: Develop robust guidelines for SBOM generation, vulnerability scanning, AI-assisted Risk Assessment and Management, and remediation. These policies must be aligned with NERC CIP standards (e.g., CIP-010 R1, CIP-013 R1 & R2). Actionable Step: Formalize your SBOM management lifecycle within your NERC CIP compliance program, detailing roles, responsibilities, and timelines.
Select and Integrate Appropriate AI Tools: Choose AI tools that fit your specific environment (on-prem OT, cloud, hybrid) and integrate them effectively with your existing security infrastructure, such as SIEM and SOAR platforms. For cloud components, tools like Wiz are invaluable; for on-prem OT, specialized OT-aware AI solutions might be necessary. Actionable Step: Pilot selected AI tools for SBOM analysis and vulnerability correlation in a representative segment of your environment to assess their effectiveness and integration capabilities.
Invest in Human Expertise and Culture: AI tools augment, not replace, human expertise. Ensure your team can interpret AI findings, validate alerts, and make informed decisions. This is especially important concerning OT-specific risks and their potential impact on BPS reliability. Actionable Step: Provide targeted Awareness and Training for security and operations personnel on leveraging AI tools for SBOM management and NERC CIP compliance.
Furthermore, it is crucial to:
Prioritize and Contextualize with AI: Use AI to help prioritize NERC CIP SBOM vulnerabilities, but always within the context of your specific BES Cyber Systems and their potential impact on reliability. Not all vulnerabilities carry equal risk in an OT setting, and AI-driven prioritization should be refined with BPS-specific operational knowledge.
Enable Continuous Monitoring and Adaptation: The threat landscape and your software inventory are constantly changing. Your AI-driven SBOM program must be continuous, with regular updates to vulnerability databases, AI models, and the SBOMs themselves. This involves establishing automated workflows for ingesting new SBOM versions and vulnerability data into your AI analysis platform. Effective Continuous Monitoring is key.
Conclusion: Building Resilience is the Only Option for NERC CIP SBOM Vulnerabilities
The evolving NERC CIP landscape and the inherent complexity of modern software paint a clear and urgent picture. Consequently, managing NERC CIP SBOM vulnerabilities is an ongoing, critical endeavor for all entities responsible for the Bulk Power System. Artificial Intelligence will play an increasingly vital role in this domain. Its algorithms are becoming more sophisticated at detection and prediction. Developers are also integrating AI capabilities more into the software development lifecycle itself. NERC CIP standards may also evolve. This evolution could mean more explicitly addressing advanced practices, such as AI-driven SBOM analysis, as the BPS becomes increasingly software-defined.
Organizations operating the Bulk Power System must recognize that addressing NERC CIP SBOM vulnerabilities is not just a compliance task; it is fundamental to national energy security and the reliable operation of critical infrastructure. AI tools, including platforms like Wiz for cloud-connected systems, offer powerful capabilities. However, their true value is realized when they are part of a holistic, risk-based cybersecurity strategy. This strategy must skillfully combine advanced technology with robust processes, diligent Audit and Compliance Management, and dedicated human oversight. Such an approach helps organizations proactively mitigate risks associated with NERC CIP SBOM vulnerabilities and ensures the continued reliability of North America’s energy infrastructure.







