From Technical Concern to Strategic Business Imperative
In today’s hyper-connected world, cybersecurity risk is unequivocally business risk. However, many organizations struggle to effectively integrate cybersecurity risk management (CSRM) with their broader Enterprise Risk Management (ERM) frameworks. This disconnect often leads to siloed decision-making, poor resource allocation, and ultimately, an increased vulnerability to costly breaches. Bridging this gap through effective Cyber Risk ERM is crucial for organizational resilience. Fortunately, NIST offers NISTIR 8286C, titled “Staging Cybersecurity Risks for Enterprise Risk Management and Governance.” This valuable roadmap provides a structured approach. Organizations can use it to aggregate, normalize, and share cybersecurity risk information. This informs leadership and strengthens governance.
This guidance helps organizations move beyond viewing cybersecurity as a purely technical concern, isolated from overarching business strategy and objectives. By implementing the principles outlined in NISTIR 8286C, businesses can achieve a more holistic understanding of their risk landscape. This enables better-informed decisions, more effective resource allocation, and a stronger overall security posture. This integration is essential not just for mitigating threats, but for enabling the organization to confidently pursue its strategic goals in an increasingly complex digital environment.
The Challenge: Why You Must Integrate Cyber Risk with ERM
Traditionally, cybersecurity was often perceived as a technical discipline separate from broader business strategy. Technical teams focused on vulnerabilities, patches, and threat actors, while executives concentrated on other categories of risk, such as financial, operational, and reputational risks. This separation inherently creates significant problems for effective enterprise-wide risk management. Senior leaders often lack a clear, consolidated view of how cyber risks specifically impact the achievement of strategic business objectives. Furthermore, technical jargon can obscure the true business implications of cybersecurity vulnerabilities.
If cybersecurity isn’t integrated into ERM, prioritizing cyber investments against other business needs is challenging. The process often becomes subjective, potentially leading to resource misallocation.
As an example, organizations may over-invest in mitigating minor technical issues. Conversely, they might neglect cyber risks that pose a high business impact, or vice versa. This siloed approach frequently results in a reactive cybersecurity posture, where organizations primarily address threats only after incidents occur, rather than proactively managing cyber risk as an integral part of their overall strategy. Furthermore, differing terminologies and metrics between technical and business teams can hinder effective communication about risk appetite, tolerance levels, and the effectiveness of mitigation efforts, making it challenging to establish a unified understanding and approach to managing Cyber Risk ERM.
NIST IR 8286C: The Framework to Integrate Cyber Risk with ERM
NISTIR 8286C is part three of a series (the NISTIR 8286 series) designed to help organizations integrate CSRM programs and information into their existing ERM processes. While previous parts, 8286A and 8286B, focused on identifying cybersecurity risks using Cybersecurity Risk Registers (CSRRs) and prioritizing those risks, respectively, 8286C concentrates on the crucial subsequent steps of aggregation, normalization, integration, communication, and oversight. This provides a methodology for “staging” cybersecurity risks, essentially translating detailed technical findings into a format that business executives and boards can understand, contextualize, and act upon.
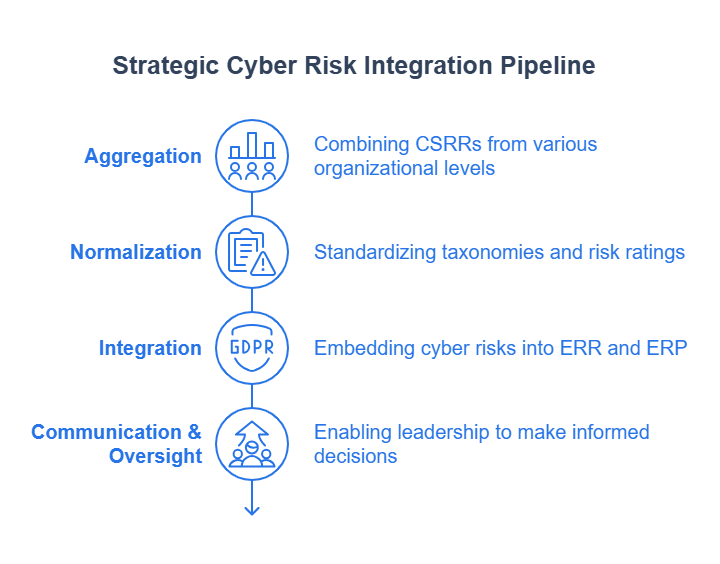
The process outlined involves several key activities:
Aggregation: Combining cybersecurity risk data from various sources and levels within the organization (e.g., system-level, department-level, business unit-level CSRRs) to create a composite, higher-level view of cybersecurity risks.
Normalization: Applying consistent criteria, taxonomies, and standardized rating schemes (for likelihood, impact, etc.) to the aggregated cybersecurity risks. This allows for meaningful comparison of diverse cyber risks across the enterprise and facilitates more consistent tracking and reporting.
Integration: Incorporating the normalized cybersecurity risk data into higher-level enterprise risk artifacts, most notably the Enterprise Risk Register (ERR) and the Enterprise Risk Profile (ERP). This ensures that they consider significant cyber risks alongside other major enterprise risks.
Communication & Oversight: Utilizing these integrated enterprise risk artifacts to inform senior leadership and boards, support governance decisions related to risk appetite and tolerance, and facilitate ongoing monitoring of the cyber risk landscape and the effectiveness of risk responses. NISTIR 8286C emphasizes that cybersecurity is just one component of overall enterprise risk and, therefore, must be managed in a manner consistent with how other significant risks to the organization are managed.
Key Concepts in NIST IR 8286C
Successfully implementing the guidance in NISTIR 8286C hinges on understanding several core concepts. Cybersecurity Risk Registers (CSRRs) are foundational documents that record detailed risk information at the system or organizational component level, including risk scenarios, impact analyses, and planned or existing response activities. NISTIR 8286C focuses on how to effectively “roll up” or aggregate information from these multiple CSRRs into a more consolidated enterprise view. As CSRR information is combined from lower levels, the identified risks must be normalized. This involves de-duplicating identical risks, grouping similar risks under common categories, applying consistent rating criteria (for likelihood, impact, and potentially risk velocity and context), and resolving disparities where similar risks might have been treated or rated differently across various business units.
The Enterprise Risk Register (ERR) is a comprehensive inventory. It lists major enterprise-level risks. This includes normalized cybersecurity risks requiring sustained management attention.
The Enterprise Risk Profile (ERP), however, is different. It’s typically a prioritized subset of the ERR. The ERP highlights the most significant risks, both cyber and non-cyber. These are risks that directly threaten strategic objectives. They might also expose the organization to unacceptable levels of mission, financial, or reputational harm. Risk governance processes set the enterprise’s objectives, define its risk appetite and tolerance, establish policies and roles for risk management, and monitor performance. NISTIR 8286C emphasizes how these governance structures direct CSRM activities and, conversely, how the results of CSRM (communicated through the ERR and ERP) feed back into governance to allow for necessary adjustments to strategy, controls, or risk appetite.
Utilizing Supporting Concepts: BIA and MEA Cycle
Several supporting concepts are also crucial for effectively staging cyber risks. A Risk Breakdown Structure can help categorize risks, for example, by primary impact areas (e.g., Mission/Operations, Financial, Reputational, Compliance), which aids in aligning cyber risks with broader enterprise objectives and facilitates communication with non-technical stakeholders. Understanding system dependencies—how various IT, OT, and IoT systems support critical business functions—is vital for accurately assessing the potential impact of cyber threats. A Business Impact Analysis (BIA) is a key process that provides this linkage between systems and business functions.
Finally, the Monitor, Evaluate, Adjust (MEA) cycle underscores that ERM and CSRM are not static, one-time activities but iterative processes. Continuous monitoring, often utilizing Key Performance Indicators (KPIs) and Key Risk Indicators (KRIs), is necessary to track the risk environment and control effectiveness. Evaluation involves comparing actual performance and risk levels against defined risk tolerance thresholds. Based on this evaluation, the organization may need to make adjustments to strategy, controls, risk appetite, or even the risk management processes themselves. This continuous feedback loop ensures that the organization’s approach to Cyber Risk ERM remains relevant and effective over time.
Practical Steps to Integrate Cyber Risk with ERM using NIST IR 8286C
Translating the guidance in NISTIR 8286C into practice requires a series of deliberate and structured steps. Organizations should establish clear governance structures. Define cyber risk ownership. This ownership should be at system, business unit, and enterprise levels. These actions ensure effective collaboration among key roles like the CISO, CRO, and business unit leaders. Developing and enforcing a common risk rating scheme and taxonomy across the enterprise is crucial. This scheme should cover likelihood, impact, and potentially risk velocity, enabling effective normalization of cyber risks from diverse sources.
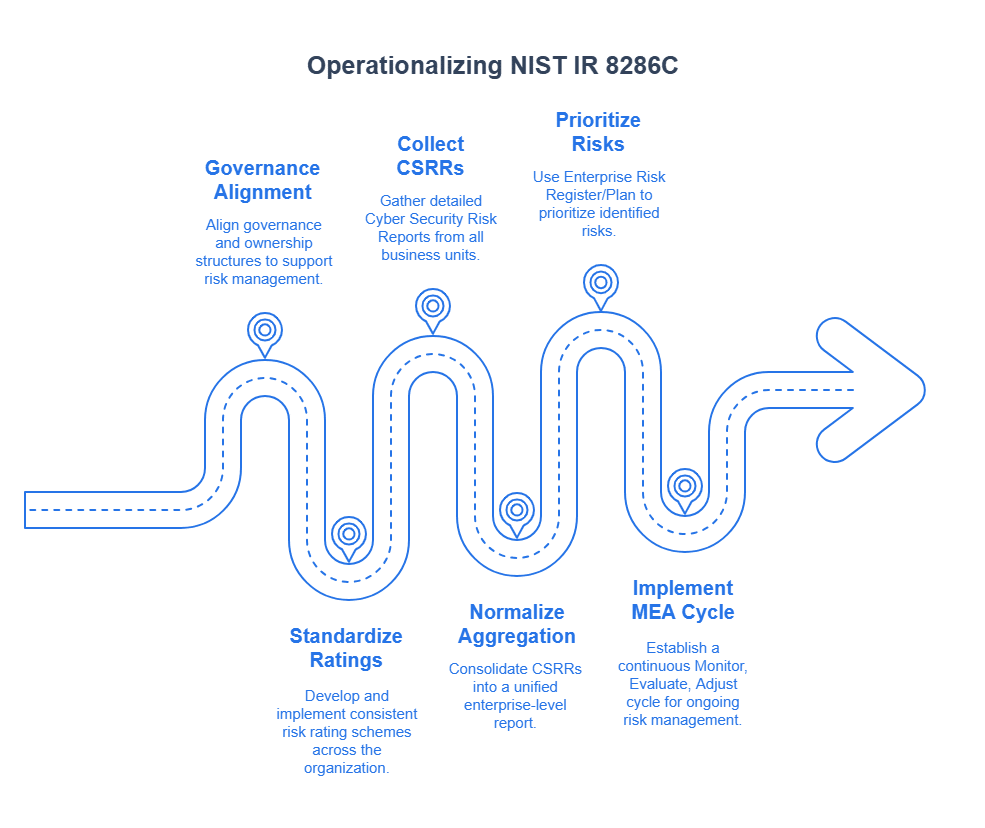
Implementing robust CSRR processes at lower levels ensures these processes capture detailed risk information. This information, including response actions and associated costs, is captured accurately and consistently. Organizations must place a significant focus on the normalization process. This involves training risk managers. They need to effectively de-duplicate, categorize, and apply consistent rating criteria. The goal: Transform numerous CSRR entries into a useful Enterprise-level CSRR (E-CSRR). Then, use the ERR as the comprehensive inventory of significant enterprise risks. Use the ERP to focus executive attention on the most critical risks—both cyber and non-cyber—that impact strategic goals. Integrating cyber risk assessments with BIA data is essential. This helps to clearly understand the potential impact of cyber threats on critical business functions. Finally, instituting a formal MEA cycle, with regular monitoring of KPIs and KRIs, evaluation against risk tolerance, and subsequent adjustments to strategy or controls, will ensure the ongoing effectiveness of the integrated Cyber Risk ERM program.
The Future of Integrated Risk Management
The imperative to effectively integrate cyber risk with ERM will only continue to grow as organizations become more digitally dependent, emerging technologies like Artificial Intelligence introduce new and complex risk dimensions, and the threat landscape constantly evolves. To navigate this future, organizations must adopt an agile, forward-looking approach to risk management. This involves a commitment to continuous improvement. It means regularly refining risk assessment methodologies, normalization techniques, and reporting mechanisms based on experience and changing conditions.
Enhanced collaboration across traditional silos is also key. A shared understanding and common language for risk are essential. This applies to IT, security, risk management, and various business units. Ultimately, cultivating a proactive, risk-aware culture where cybersecurity is viewed as everyone’s responsibility, from the boardroom down to the front lines, will be critical for sustained success in managing the multifaceted challenges of Cyber Risk ERM in the years to come.
Conclusion
NISTIR 8286C offers an invaluable framework for organizations seeking to mature their risk management practices. It achieves this by effectively staging cybersecurity risks for an enterprise-wide view. Applying core principles like aggregation, normalization, and integration—supported by continuous monitoring and strong governance—is key. This allows businesses to holistically understand their cyber risk posture and its potential impact on strategic objectives. This integrated view enables better-informed decision-making and more effective resource allocation. Ultimately, it leads to greater organizational resilience against the evolving cyber threat landscape.
Moving beyond manual processes and disparate spreadsheets is crucial for successfully operationalizing these principles. A structured approach, often supported by specialized GRC or ERM platforms, can provide the necessary automation, centralization, and reporting capabilities to truly integrate cyber risk with ERM, turning NIST’s guidance into a sustainable and effective operational reality.







