Protecting Critical Infrastructure: The New Framework
The digital world evolves rapidly, compelling cybersecurity professionals to diligently protect data and systems. This vigilance is especially critical for Operational Technology (OT), where robust guidelines like NIST SP 800-82r3 are indispensable. Consider the smooth functioning of critical infrastructure – power grids delivering electricity, water treatment facilities ensuring clean water. The uninterrupted operation of these environments is paramount. This article explores how to harmonize OT Security and IT security, forging a stronger security posture and preventing potential disruptions.
This piece delves into this complex area, exploring the connection between NIST SP 800-82r3 and effective risk mitigation. It serves as a reference for coordinating security across operations, blending best practices with practical approaches to systematically reduce vulnerabilities and bolster defenses. This proactive stance is vital for safeguarding our essential services. The increasing sophistication of cyber threats against industrial environments makes understanding and implementing NIST SP 800-82r3 more critical than ever.
NIST SP 800-82r3: Your Essential OT Security Guide
NIST Special Publication 800-82r3, titled “Guide to Operational Technology (OT) Security,” is a primary reference for structuring effective OT security strategies. Developed by the National Institute of Standards and Technology (NIST), a renowned authority, this guide provides customized recommendations suited to OT-specific challenges. Unlike generic advice, NIST SP 800-82r3 helps organizations navigate the unique complexities inherent in securing these often-overlooked yet critically important systems. Understanding the OT landscape, much like carefully planning a building’s foundation, is the foundational step to securing it. A key objective of NIST SP 800-82r3 is to provide a clear pathway for organizations to improve their OT cybersecurity capabilities by offering specific controls, architectures, and processes.
Unlike typical IT systems that primarily deal with data, OT environments control the physical world. They directly monitor and manage physical processes; in fact, they are the control systems behind critical infrastructure. This direct physical impact makes them attractive targets for malicious actors, from state-sponsored groups to cybercriminals seeking to cause disruption or financial gain. Consequently, NIST SP 800-82r3 offers detailed advice and actionable recommendations covering key areas for OT Security. Pivotal areas include Risk Assessment and Management frameworks, resilient security architecture design, and effective Incident Response. Mastering these elements is essential to protect invaluable OT systems from a growing array of threats. The publication emphasizes a life cycle approach to security, considering all phases from design and implementation to operation, maintenance, and eventual decommissioning of OT systems.
Deciphering Key Aspects of NIST SP 800-82r3 for OT Security
This comprehensive guide provides a holistic framework for OT Security. Let’s break down its significant components.
The Risk Management Framework section provides strategic direction for addressing OT security risks. OT environments can present complex and unpredictable risk scenarios, often involving legacy systems and unique communication protocols. NIST SP 800-82r3 details a structured approach to identify system vulnerabilities, assess threat likelihood and impact, and then outline an actionable plan to reduce risk exposure. This involves identifying critical assets within the OT environment, understanding potential attack vectors (both cyber and physical), and evaluating the potential consequences of a security breach on safety, operational continuity, and regulatory compliance. This is not a one-time task but an ongoing evaluation and adaptation process, crucial for maintaining resilience as threats evolve and OT systems change.
The Security Architecture section outlines the design principles for OT defenses. It emphasizes layered security controls (often referred to as defense-in-depth) and strategic Network Security including network segmentation to isolate critical components. For instance, creating distinct zones for control systems, safety instrumented systems (SIS), and connections to enterprise networks can limit the lateral movement of an attacker and contain the impact of a breach. This approach establishes a multi-layered security structure to protect critical assets, ensuring multiple defense layers work to thwart potential intrusions. NIST SP 800-82r3 advocates for architectures that are not only robust but also resilient, meaning they can withstand or quickly recover from attacks while maintaining essential functions.
Regarding Incident Response, when a security incident occurs, a swift and effective response is critical to minimize damage and restore normal operations. The guide provides essential procedures to detect security incidents in OT systems, analyze their nature and scope, contain the breach to prevent further spread, eradicate the threat, and recover affected systems and processes. This minimizes disruption and impact on production, safety, and the environment. For example, having pre-defined communication channels with stakeholders and technical procedures for isolating affected network segments can significantly speed up containment. A well-rehearsed Incident Response plan, specifically tailored to the unique characteristics and priorities of OT environments (such as prioritizing safety and availability), can be the difference between a minor hiccup and a major crisis. This also includes post-incident analysis to learn from the event and improve future responses and preventative measures.
Finally, the Control Baselines section represents minimum security requirements and defines specific controls applicable to OT systems. NIST SP 800-82r3 categorizes these baselines based on system criticality (e.g., high, medium, low impact) and their potential impact if compromised. For example, a system controlling a critical manufacturing process or a safety-critical function will have more stringent control requirements than a less critical monitoring system. These baselines, which cover technical, operational, and management controls, serve as fundamental building blocks. They are essential for establishing a strong security foundation and help organizations apply a consistent and appropriate level of security across diverse OT assets, ensuring that protective measures are commensurate with risk.
IT and OT Security: Combining Worlds for Enhanced Protection
In today’s interconnected landscape, OT environments increasingly intertwine with IT networks. This convergence offers significant benefits, such as boosted efficiency through real-time data, enhanced data analytics for process optimization, and remote management capabilities for maintenance and support. However, it concurrently expands the attack surface, introducing new cybersecurity risks that many legacy OT systems were not originally designed to handle. Consequently, relying solely on traditional IT security measures, which often prioritize confidentiality, is insufficient. The OT realm distinctively prioritizes availability and safety above all. Applying only IT-centric security methods leaves OT environments vulnerable, as these methods may not address the specific protocols, operational constraints, or safety implications inherent in industrial control systems.
Harmonizing IT and OT security is crucial for several reasons:
Connected Systems: OT systems now frequently link to IT networks. This integration facilitates valuable capabilities like remote access for maintenance by specialized technicians, real-time data exchange for operational insights that feed into enterprise resource planning (ERP) systems, and seamless business process integration for better overall decision-making.
Evolving Threats: As OT systems become more connected, attackers continuously refine their approaches and develop sophisticated tools to target them. Their intentions range from industrial espionage aimed at stealing intellectual property, deploying ransomware that can halt production, to establishing advanced persistent threats (APTs) that can cause long-term damage, subtle manipulation of processes, or disruption of critical services.
Real-World Impact: Cyberattack consequences in OT can be devastating and extend beyond data loss. They can disrupt critical infrastructure, leading to power outages, contamination of water supplies, failure of transportation systems, or compromised safety systems, potentially resulting in environmental damage, injury, or even loss of life. Organizations also face significant financial repercussions from downtime, recovery costs, regulatory fines, and severe reputational damage.
Therefore, a holistic cybersecurity strategy that considers the unique requirements, operational contexts, and risks of both IT and OT domains is no longer a luxury but a fundamental necessity for comprehensive protection. This strategy must be championed by leadership, understood throughout the organization, and supported by adequate resources and expertise.
Harmonizing with Risk Mitigation: Taking Decisive Action for OT Security
To effectively harmonize OT security, taking decisive action through robust risk mitigation is absolutely essential. This involves a proactive and continuous process aimed at reducing both incident likelihood and potential impact, drawing upon the foundational principles within NIST SP 800-82r3 for maximum protection.
The fundamental steps begin with identifying and evaluating risks. First, conduct a thorough risk assessment specifically for your OT systems. This involves identifying all OT assets (hardware, software, data). Next, understand their specific vulnerabilities. These can differ significantly from IT vulnerabilities due to legacy components or proprietary protocols. Then, evaluate potential threat vectors. These include internal threats (like insider actions or accidental misconfigurations) and external threats (like malware or targeted attacks). Finally, create an effective action plan. Use the Risk Assessment and Management framework within NIST SP 800-82r3 as your guide. This assessment should be periodically reviewed and updated to reflect changes in the threat landscape or the OT environment itself.
Apply appropriate security measures and implement robust security controls based on your risk assessment, following NIST guidance. This typically includes measures like Network Security through network segmentation to isolate critical control networks from business networks, strict Identity Management and Access Control using principles like least privilege and role-based access, and potentially the deployment of industrial Intrusion Detection/Prevention Systems (IDS/IPS) specifically designed for OT protocols and traffic patterns. Additionally, having well-documented and tested Incident Response plans is essential.
To strengthen this approach, consider implementing a dedicated Posture and Vulnerability Management strategy. This allows your organization to continuously identify, prioritize, and remediate vulnerabilities within OT environments. This ensures risks are not only discovered but actively managed and mitigated. This includes regular vulnerability scanning. Use OT-safe tools and techniques that won’t disrupt operations. A structured patching process is also essential; it must balance security needs with operational stability. Finally, employ configuration management to ensure systems remain in a secure state.
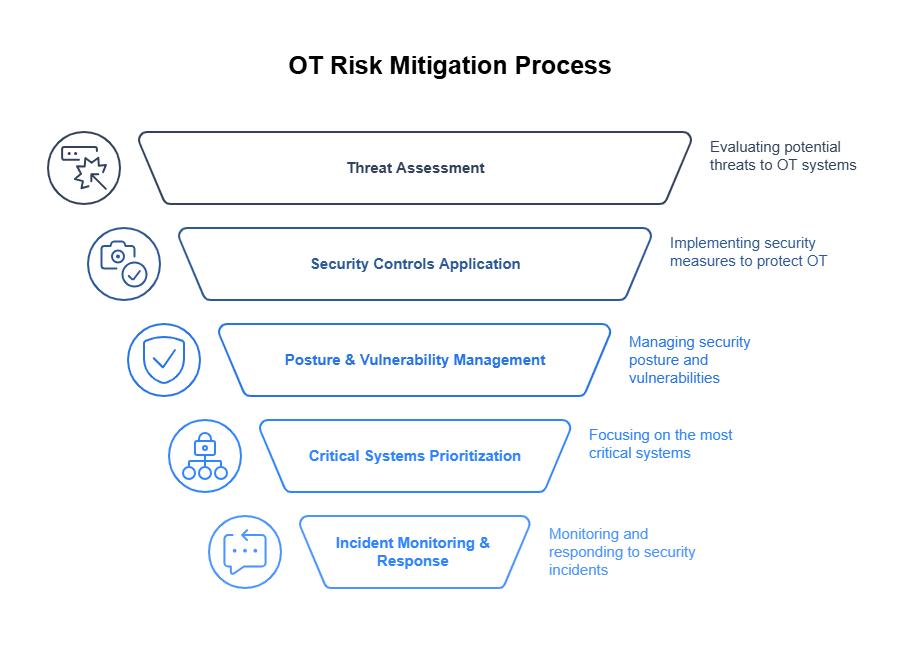
Subsequently, prioritize important resources. Not all assets carry the same level of risk or criticality to the operation. Therefore, focus protective efforts on the most critical resources. These include OT systems directly controlling physical processes. Also, prioritize safety instrumented systems designed to prevent hazardous conditions. The integrity of the control framework itself is another key area. Ensure Continuous Monitoring of OT performance, network traffic, and security logs for any anomalies or indicators of compromise. This helps in early detection and response.
Following that, you will need to monitor and detect threats. Establish robust Logging and Threat Detection capabilities and Continuous Monitoring practices. It is important to recognize suspicious activity promptly and act on these alerts decisively. This often involves Security Information and Event Management (SIEM) systems. Ideally, these systems are tailored or configured to understand OT-specific elements. These elements include logs, protocols (like Modbus, DNP3, or EtherNet/IP), and event types. This understanding provides context relevant to industrial operations.
Then, build and refine incident response plans. Develop, document, and regularly test incident response strategies. Use tabletop exercises or simulations for testing. These strategies must address the unique nuances of OT systems. These plans must include clear containment processes. For example, they should detail how to isolate a compromised segment without unsafely disrupting essential services. The plans also need eradication steps to remove the threat. Finally, include recovery procedures to restore operations safely and efficiently, verifying system integrity before going back online. By diligently following these fundamental actions, organizations can significantly strengthen their OT security posture and systematically reduce their overall risk exposure.
Practical Tips for Boosting Your OT Security
Building a robust security culture is key, extending beyond merely applying technical measures, for the best OT protection. As a result, here are practical tips to improve your organization’s OT security posture, as emphasized by principles within NIST SP 800-82r3:
Create Clear Security Rules and Policies: Develop, document, and clearly communicate security policies and procedures specifically tailored for the OT environment. These should govern aspects like data access, change control management for OT systems, incident reporting and response protocols, secure remote access, and ensure clear roles and responsibilities are defined for all personnel.
Build Security Awareness and Training: Consistently perform Awareness and Training for all personnel interacting with OT resources. This includes operators, engineers, maintenance staff, and even third-party vendors who may access OT systems. Educate your team on OT security. They must understand its importance. They also need to learn how to recognize potential threats (like phishing emails or unusual system behavior). Finally, cover the correct procedures for reporting suspicious activity or concerns
Use Strong Verification and Authorization Processes: Enhance protection from unauthorized OT activity by rigorously enforcing strong authentication mechanisms, such as multi-factor authentication (MFA) where feasible and appropriate for the system, and implementing strict authorization protocols based on the principle of least privilege. This ensures users and systems only have the access necessary to perform their designated functions.
Apply Updates and Patches Reliably: Establish a disciplined and risk-based patching process. Reliably test security patches and firmware updates. Use a non-production environment for this testing, if one is available. Only then should you apply them to live OT systems and components. This can be challenging in OT environments, often due to uptime requirements and compatibility issues. To manage known vulnerabilities, a structured approach is essential. This involves vendor coordination, thorough testing, and scheduled maintenance windows.
Monitor System Activity and Security Logs: Implement robust tools and processes to collect, analyze, and report on security data from OT systems. This Continious Monitoring is vital for early detection of potential compromises, operational anomalies that might indicate a security issue, and aids significantly in forensic analysis should an incident occur. Ensure logs are securely stored and regularly reviewed.
Approaching OT Security: What’s Next on the Horizon?
As industrial systems become increasingly interconnected and sophisticated, organizations must adapt their security planning to tackle emerging difficulties and evolving threats. NIST SP 800-82r3 provides a strong foundation, but awareness of future trends is also crucial for long-term resilience. Here are a few significant trends shaping the future of OT security:
Consider the Evolving Industrial Internet of Things (IIoT). This field is rapidly growing, involving a multitude of connected sensors, actuators, smart devices, and edge computing nodes deployed throughout industrial facilities. Consequently, this dramatically expands potential attack vectors and increases the complexity of asset management and security monitoring. To secure the IIoT, new and scalable security measures are required. These must emphasize secure device lifecycle management (from provisioning to decommissioning). Additionally, ensure robust authentication and encryption for all connected devices. Network segmentation strategies are also vital for isolating IIoT devices.
Cloud Integration for OT Data and Analytics is becoming more prevalent. The cloud offers scalability and powerful analytical capabilities. These capabilities aid process optimization and predictive maintenance. It also enables remote access for monitoring and control (with appropriate safeguards). Centralized data storage is another key feature. Therefore, it is essential to address the associated vulnerabilities related to secure data transfers to and from the cloud, ensuring secure cloud storage configurations, and managing Identity Management and Access Control in hybrid IT/OT/cloud environments. Data classification, encryption (in transit and at rest), and clear responsibility models for cloud security are critical.
The Threat Landscape Constantly Evolves. Attackers are relentless and innovative. Their methods include developing new malware strains (such as ransomware specifically targeting ICS). They also exploit novel vulnerabilities. Furthermore, they use sophisticated techniques to infiltrate and disrupt industrial control systems. Organizations must continuously refine security measures and leverage threat intelligence feeds relevant to the OT sector and their specific industry. Additionally, they should adopt adaptive security architectures that can recognize and protect against these emerging, often targeted threats. Proactive threat hunting and participation in information sharing and analysis centers (ISACs) can also bolster collective defense.
Look at Generative AI Applications in Security. Generative AI holds significant potential to enhance cybersecurity operations, for instance, by automating aspects of Logging and Threat Detection through more sophisticated anomaly identification, assisting in initial incident response by suggesting containment actions, or even generating synthetic data for more effective security testing. While AI’s capabilities will improve and integrate into security toolsets, organizations face risks. They must be aware of adversarial AI uses, such as AI-powered attacks. AI-driven security tools must be robustly tested and validated for the specific OT environment. Human oversight is also essential, particularly in critical decision-making.
Next Steps: Securing Your Operational Future with OT Security
Making IT and OT security function harmoniously, guided by frameworks like NIST SP 800-82r3, is a fundamental necessity in the modern industrial landscape. This synergy defends your organization against evolving threats, prevents the loss of critical operational capabilities, and safeguards valuable information and physical processes. You can secure your operations by combining the principles outlined in NIST SP 800-82r3 with well-honed risk mitigation strategies, a commitment to continuous improvement, and strong leadership support.
Remember, achieving robust OT security is an ongoing journey, not a one-time destination. It requires sustained effort. You must also adapt to new technologies and threats. Foster a culture of security awareness throughout the organization. This culture should extend from the plant floor to the executive suite. Start building your resilient cybersecurity future today. Understand and implement these crucial protective measures. This will help you meet your OT security goals and ensure your operational environment’s safety, reliability, and integrity.







