Protecting Customers by Shifting the Security Burden
For many years, standard software industry practice has involved a burdensome process. Organizations purchase products. Then, they must immediately undertake extensive patching, complex hardening, and numerous configurations. All this is just to achieve basic security. This reactive model, where the security responsibility largely falls on the end-user, is increasingly being recognized as unsustainable in the face of sophisticated and persistent cyber threats. A fundamental and necessary shift is underway, championed by global cybersecurity agencies, including the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI). This evolving philosophy is termed Secure by Design.
Secure by Design represents a significant rethinking of where the primary responsibility for security should lie. It advocates for moving away from placing the main onus on the customer and instead, holding software manufacturers accountable for developing and shipping products that are inherently safe and secure from their inception. This proactive approach aims to build security into the very fabric of software, rather than treating it as an afterthought. This article will explore the core principles of Secure by Design, explain why they are critical for reducing your organization’s cyber risk, and discuss how organizations can advocate for a higher standard of security from their software vendors. The widespread adoption of these principles is essential for creating a more resilient digital ecosystem.
The Challenges of “Vulnerable by Design” Software
Historically, many software products have effectively been “vulnerable by design.” Products were often rushed to market with insecure default settings, known but unaddressed vulnerabilities, and features that prioritized convenience or rapid deployment over robust security. Consequently, the customer inherited the technical debt associated with these shortcomings and, more importantly, the ensuing risks. This approach has perpetuated several challenges for end-user organizations.
One significant issue is the continuous “patching treadmill.” As detailed in NIST SP 1800-31B, “Improving Enterprise Patching for Resiliency,” organizations find themselves in a constant state of reaction, racing to apply patches for vulnerabilities that ideally should have been identified and eliminated during the software development lifecycle. This reactive patching is not only costly and resource-intensive for customers but also leaves a persistent window of opportunity for attackers to exploit known flaws before patches can be deployed.
Another challenge arises from the burden of hardening guides. Manufacturers often attempt to offset their insecure default configurations by publishing lengthy and complex “hardening guides.” As highlighted in the CISA-led international whitepaper, Shifting the Balance of Cybersecurity Risk: Principles and Approaches for Secure by Design and Default, these guides are frequently overly complex, difficult for customers to locate, and often assume a level of cybersecurity expertise that many organizations, particularly smaller ones, may not possess. This effectively creates an additional cost, or “insecurity tax,” that customers must bear in terms of time, resources, and specialized personnel needed to implement these recommendations.
Furthermore, an ever-expanding attack surface results from insecure defaults, unpatched systems, and common misconfigurations. Each of these elements provides potential entry points for malicious actors, making it easier for them to compromise systems and data. This reactive and customer-burdened model has been a primary driver of many security incidents. However, the principles of Secure by Design offer a more effective path forward.
Understanding Secure by Design and Secure by Default
Secure by Design and Secure by Default are two intertwined philosophies aimed at reversing the trend of vulnerable software. They mandate that security isn’t an optional feature developers ‘bolt on’ post-production. Instead, developers must integrate it as a foundational component throughout the entire development process and product lifecycle.

Secure by Design means that technology products are architected and engineered from the outset to reasonably protect against malicious cyber intrusions and other security threats. This approach treats security as a core business goal, deeply weaving it into every stage of the Software Development Lifecycle (SDLC). This requires software manufacturers to make strategic investments in secure development practices, employ skilled security professionals, and sometimes make difficult trade-offs, prioritizing features and configurations that protect customers over those that might seem appealing but could unnecessarily enlarge the attack surface or introduce new risks.
Secure by Default is the practical application and outcome of the Secure by Design philosophy. It means manufacturers deliver products as securely as possible ‘out of the box.’ They enable the most critical security controls by default. This is at no additional cost to the customer. For example, we should not view essential security features like multi-factor authentication (MFA) or robust logging capabilities as premium add-ons. Instead, vendors must include them as standard, non-negotiable elements. Security should be an inherent quality of the product, not an optional extra.
The Three Core Principles of a Secure by Design Philosophy
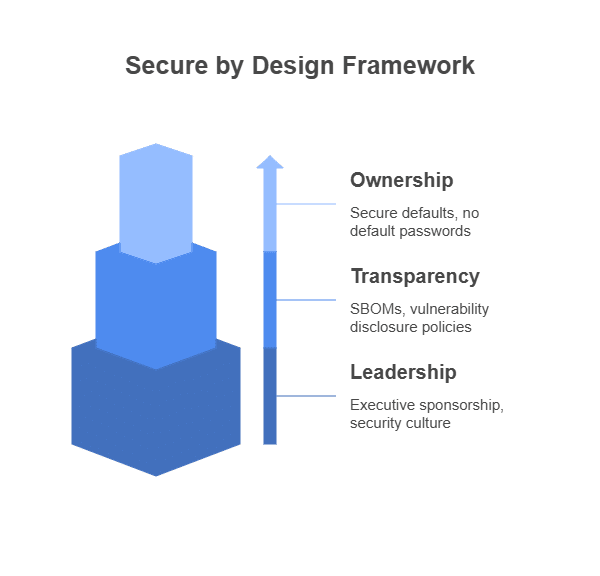
CISA and partner agencies advocate for three core Secure by Design principles for software manufacturers. Understanding these helps customers demand safer products.
Take Ownership of Customer Security Outcomes: Manufacturers are primarily responsible for their customers’ security outcomes. The burden of secure operation shifts from the consumer to the producer, with security built-in during design and development. Eliminate default passwords, require strong unique passwords at setup, and ship products with secure configurations enabled by default. Any guidance should focus on why a customer might reduce security, with clear risk warnings.
Embrace Radical Transparency and Accountability: Trust is built on manufacturers being open about their secure development practices, security features, and vulnerability handling. This helps customer decision-making and raises industry standards. Formally attest to using a secure software development framework (like NIST SSDF). Provide Software Bills of Materials (SBOMs) for visibility into software components. Maintain a clear Vulnerability Disclosure Policy (VDP) for reporting flaws.
Lead from the Top:
A robust secure development culture must be a top-down business priority, driven by executive leadership, not just a technical effort. Appoint a senior executive as the program sponsor. Realign developer incentives to include security outcomes alongside traditional metrics. Foster a culture where security is everyone’s responsibility, encouraging open communication and investment in security training.
Making Secure by Design a Reality in Your Organization
As a customer, your organization holds considerable influence to accelerate this industry-wide shift towards Secure by Design. You can create a strong ‘secure by demand’ culture. Do this by embedding these principles into your procurement processes and vendor risk management programs. This culture signals to the market that security is a non-negotiable requirement.
Consider asking direct and evidence-based questions during your procurement process. Instead of simply asking if a product is secure, request tangible proof. Inquire if the vendor can provide their completed and signed CISA Attestation Form or an equivalent self-attestation against the NIST SSDF. Ask for access to the SBOM for the product under consideration. Inquire about who the executive sponsor is for their Secure by Design initiatives. Critically, ask if they charge extra for essential security features like Single Sign-On (SSO), MFA, or comprehensive audit logging, as these should ideally be standard.
Update your vendor risk management program to make Secure by Design principles a cornerstone of how you evaluate both new and existing vendors. If a vendor cannot satisfactorily answer the questions above or demonstrate a commitment to these principles, you should consider that vendor a higher risk. Furthermore, advocate for and implement a Zero Trust Architecture within your own organization. The principles of Secure by Design align perfectly with a Zero Trust mindset, as both philosophies assume that breaches are possible and therefore emphasize building in resilience, verifying explicitly, and applying least privilege access from the start. Prioritize vendors that design and build products to operate effectively and securely within a Zero Trust environment.
The Future is Secure, By Design
The traditional model of reactive cybersecurity has proven insufficient and costly. It forced customers to bear the primary burden of securing often inherently insecure products. Consequently, organizations face an overload of patching and configuration. Increasingly sophisticated attackers also outmatch them. This unnecessarily exposes organizations to significant cyber risks. The path forward is clear. First, manufacturers must build software securely from the ground up. Second, they must take genuine ownership of their customers’ safety and security outcomes. Third, they will provide robust security by default. This is a non-negotiable right, not a luxury add-on.
By understanding and advocating for Secure by Design principles, organizations can play a pivotal role in driving this essential transformation, leading to a safer and more resilient digital infrastructure for everyone.







